LLMNR Poisoning Attack
Overview
Link-Local Multicast Name Resolution (LLMNR) is a feature used to identify hosts when DNS fails. It functions similarly to DNS by resolving IP addresses of active directory hosts, but unlike DNS, it is only used as a fallback when DNS resolution is unsuccessful. In other words, if DNS is not functioning or does not have the domain name or IP entry, LLMNR is employed.
LLMNR replaced the previously used NetBIOS Name Service (NBT-NS) technology. Windows systems typically have both LLMNR and NBT-NS enabled, and if LLMNR is not enabled, NBT-NS may still be active. Therefore, this attack can be exploited with either of these protocol unless both are disabled.
LLMNR Poisoning
In LLMNR Poisoning, our objective is to intercept and manipulate network traffic by poisoning the LLMNR protocol. By doing so, we redirect LLMNR requests to our machine instead of the legitimate server, allowing us to capture sensitive information or carry out malicious activities. This attack resembles ARP Poisoning, where we perform a Man-in-the-Middle (MITM) attack to control and manipulate network communication.
What we achieved by doing this?
LLMNR operates by sending username and NTLMv2 password hash in its requests. When we intercept network traffic, any LLMNR request containing a user's password hash becomes visible to us. This presents an opportunity to potentially crack the hash and uncover the user's password.
We utilize the Responder tool to facilitate LLMNR attacks. The syntax for running the tool is as follows:
python Responder.py -i eth0 -rdwIn the above command:
Responder.pyis the Python version of the Responder tool.-iis to specify the network interface to intercept traffic i.e. eth0, tun0, etc.-ris used to enable answers fornetbioswredir suffix queries that trick target into sending authentication information i.e. username and NTLMv2 hash.-dis used to enable answer netbios domain suffix queries.-wis used to start the rogueWPADproxy server.
Note: Instead of the Python version, you can also utilize the stand-alone version of Responder that comes pre-installed with Kali Linux.
Once the Responder server is running and intercepting traffic, any received responses can be analyzed. To attempt cracking the passwords, you can employ tools like hashcat, using the appropriate command.
Where:
-mis used to specify the hash type number i.e.5600that is for theNetNTLMv2hash.hashes.txtis the text file that contains the hash that we want to crack.rockyou.txtis the password wordlist in which we want to crack the password.
The Responder output should look like this if they capture any response.
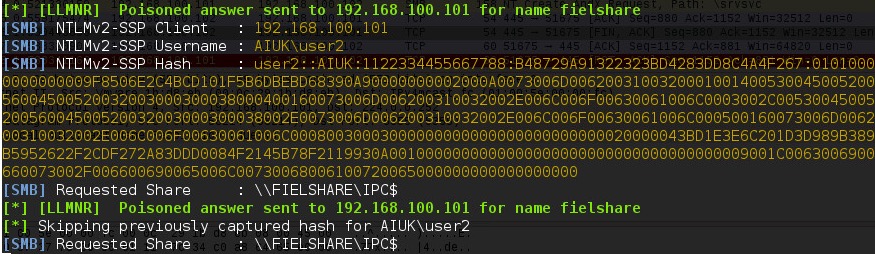
If the user password is weak then you will be able to crack it and use that password to login to the system and do other stuff.
For hash cracking we cannot expect the user always has a weak password, Cracking those hash take too much GPU or system resources so keep in mind that if you know the system doesn't have a weak password and you still use a simple password list that doesn't based on the users profile then you just waste your time and system resources. So use more user's based wordlists to get the best chances of success.
On the defensive side, this attack technique is well known by the blue teams and they have known signatures to detect LLMNR Poisoning attacks. In a Pentest sometimes we didn't care a lot about being detected but if you are on a Red Team Engagement in which being undetected is a key objective, you should be careful to use this attack.
Last updated