The advent of Cyber 1 (2019)
Task 1 Introduction

[The Story]
Just before the lead-up to Christmas, Santa’s company(The Best Festival Company) has been compromised by his nemesis(The Christmas Monster). Luckily, one of Santa’s elf team has a background in security. Can they recover all their systems before the lead-up to Christmas?
It’s the evening of 30th November - the air in the arctic circle is filled with excitement, as every year. This year has been even smoother than previous years - Santa’s digitalization program has made lives easier for everyone in the company. Elf McElferson, the CTO of the arctic circle, starts doing a couple of last-minute checks; everything has to be operating successfully running up to Christmas. With her warm hot chocolate next to his desk, all she needs to do is open the health dashboard and grin at all the green lights. She enters the URL on the dashboard and leans closer to the screen, anxiously waiting for confirmation. The page loads faster than expected and she gets the initial glimpse of all green. Wait, the first indicator moves to red, and every other one follows the same.
In less than a minute, she and all her colleagues receive the following email:
Hey, Crew! We know that this is the busiest time of your year. What a shame though - it looks like all of you are locked out of your systems and can’t do any work. Boo hoo for Christmas Santa’s Fav Nemesis, Christmas Monster
McElferson jumps out of her seat and yells. This cannot be happening. How is she supposed to fix this - it’s only 25 days till Christmas and no one can do anything. She goes to the only person who knows about security on his team, Elf McSkidy(you) and asks them to use their l33t skills to fix this. They clearly have a big task ahead of themselves.
A new task will be revealed every day, and each task will be independent of the previous one. These challenges will cover the following topics:
Linux Security
Web Application Security
Network Security
Reverse Engineering
Forensics
The challenges are designed for beginners and assume no previous knowledge of security. For more information on Prizes, Swag, and event details please check out the Christmas page.
By completing these challenges, you give your consent to give your email to CompTIA (the competition sponsor)
Task 2 Connect To Our Network

When you deploy a machine on TryHackMe, you will need to be connected to our network using an OpenVPN client.
Information on connecting to our network and downloading your connection pack can be found on the access page.
If you have problems connecting, please email us or ask on Discord!
Task 3 Points don't matter

In this competition, points do not matter. Your leaderboard rank will not affect you.
For each task you get correct, you get a raffle ticket. On the 26th of December, we will choose the winners randomly using everyone's raffle tickets.
Also, every day you complete a challenge, you get entered into another prize draw, for the chance to win a mini-prize. The 'Daily Prizes' are done at the end of the week.
Task 4 Our Socials
 ](https://discord.gg/GzVZtGX)
](https://discord.gg/GzVZtGX)
Be a part of our growing community and join our discord!
 ](https://twitter.com/RealTryHackMe)
](https://twitter.com/RealTryHackMe)
Follow us on Twitter to receive daily challenge posts.
We will choose a random winner every day, to enter and simply complete the challenge released on that day. All winners will be announced via Twitter.
Task 5 [Optional] Your own Kali Linux Machine
 ](https://tryhackme.com/room/kali)
](https://tryhackme.com/room/kali)
If you don't have the right desktop environment or security tools on your computer, you can deploy and access your own Kali Linux machine directly in your browser. This also removes the need to be connected to our OpenVPN server!
You need to be subscribed to do this.
If you don't want to subscribe, each task will run through the tools needed and how to set them up on your local machine.
Task 6 [Day 1] Inventory Management

Elves needed a way to submit their inventory - have a web page where they submit their requests and the elf mc inventory can look at what others have submitted to approve their requests. It’s a busy time for my inventory as elves are starting to put in their orders. mc inventory rushes into McElferson’s office.
I don’t know what to do. We need to get inventory going. Elves can log on but I can’t actually authorize people’s requests! How will the rest start manufacturing what they want?
McElferson calls you to take a look at the website to see if there’s anything you can do to help. Deploy the machine and access the website at http://<your_machines_ip>:3000 - it can take up to 3 minutes for your machine to boot!
Supporting material for the challenge is here!
Answer the questions below
Q1: What is the name of the cookie used for authentication? A authid Solution When you go to the page there you can see the page like this
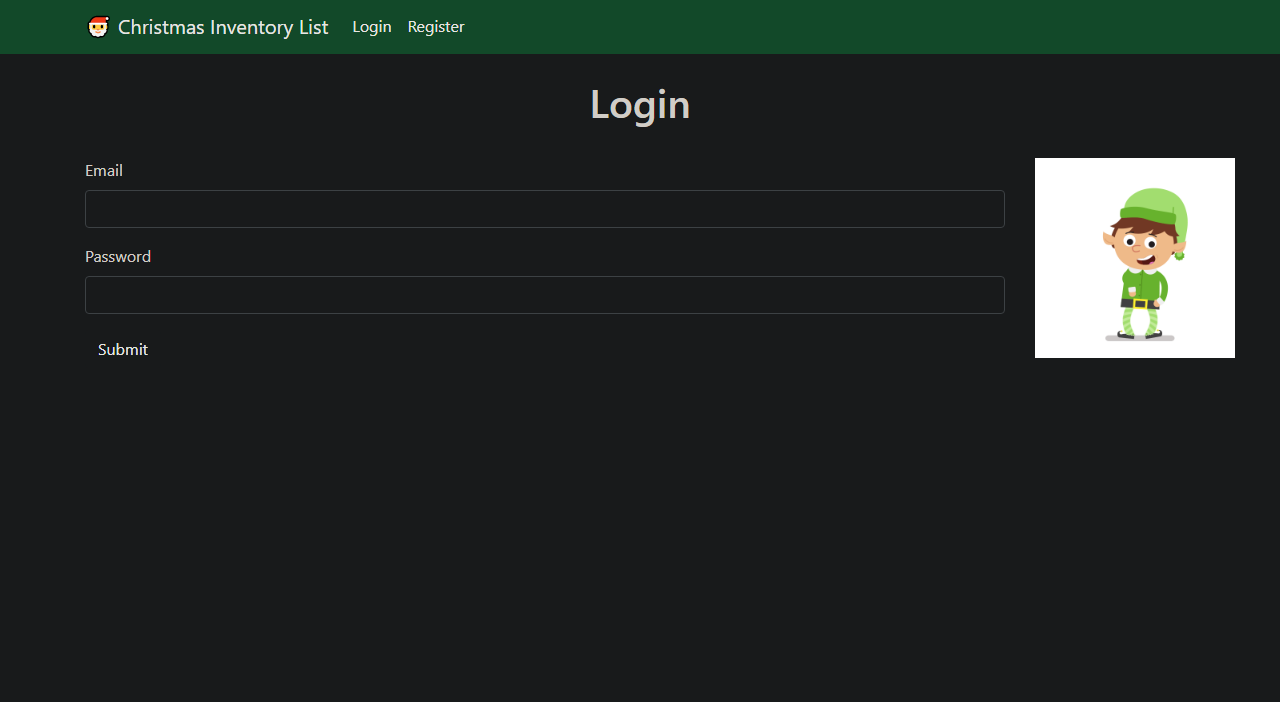
There you can see you have to log in to the account but you don't know the credentials so you can make your own account on the register section so go there and they are something like this
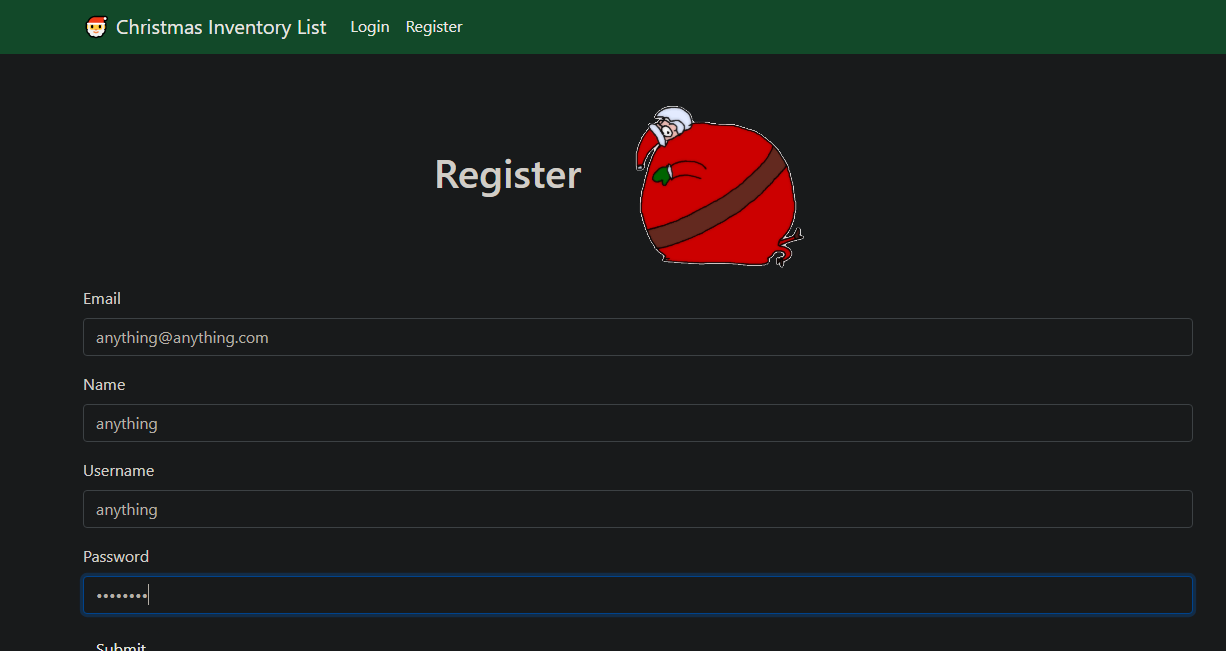
You can fill the forum with any values you want and login into that account.
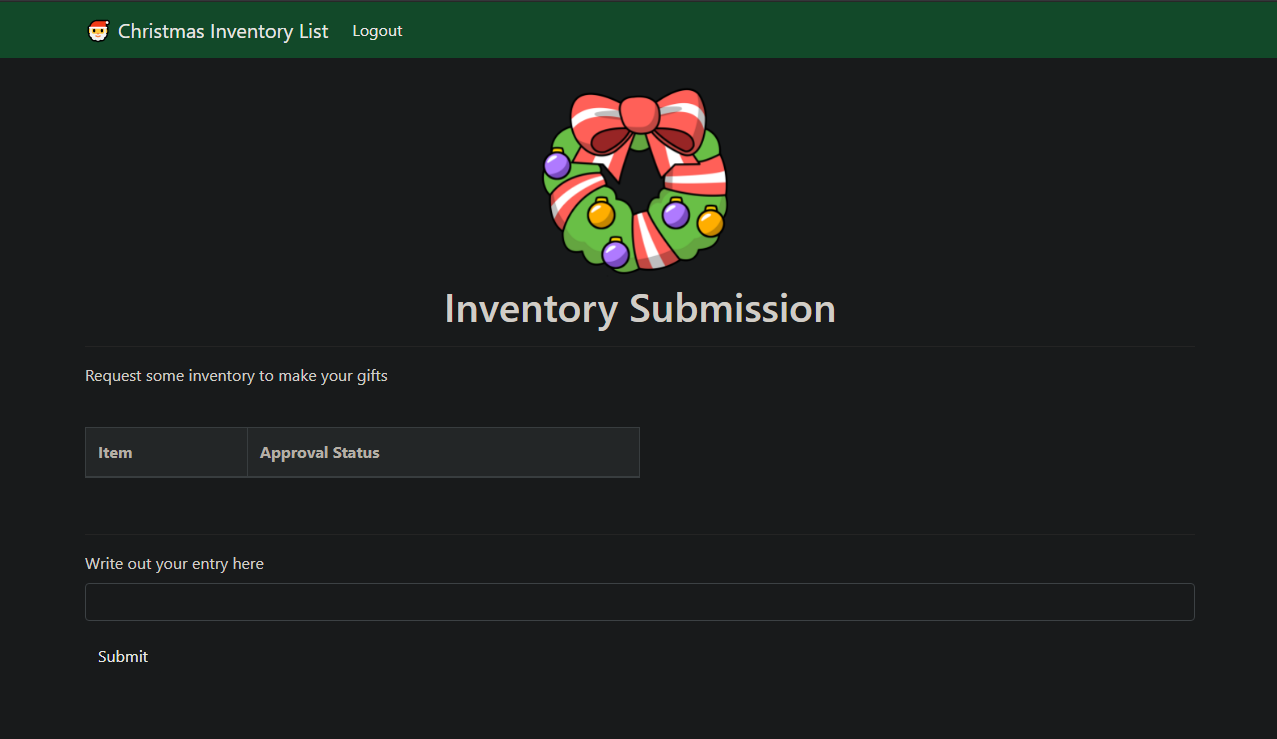
Now you log in so we can see the cookie of the user we own I'm using Chrome browser if you are using something else search how to view cookies in that browser. In Chrome go to the search bar/URL bar
Click on Not Secure
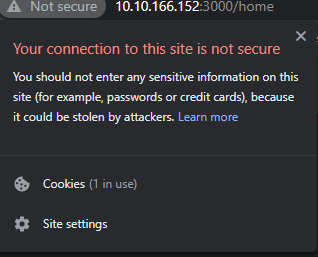
Click on Cookies and you got the cookie and there values
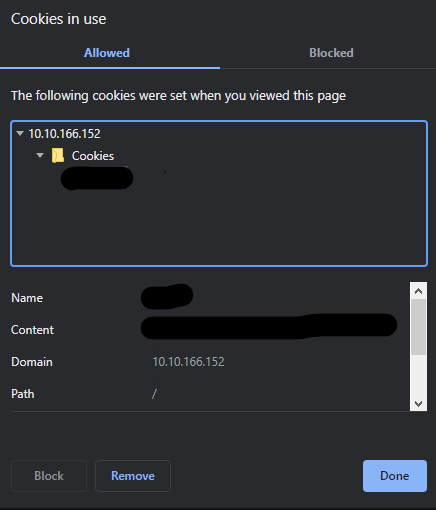
Q2: If you decode the cookie, what is the value of the fixed part of the cookie? A: v4er9ll1!ss Solution Copy the cookie value of whatever they are they are encoded with base64 encoding so we can decode it with base64 decoder on Kali Linux or also we can use an online website also from here I use Kali
This will decode that cookie and we can see there cookie first contain our username that we input on the register section and then they have some fixed input and our answer
Q3: After accessing his account, what did the user mc inventory request? A: firewall Solution From the previous question we see the server give a cookie in base64 encoded and their format is like this
So by knowing this we can abuse this to get the mc inventory account with the knowledge we have like
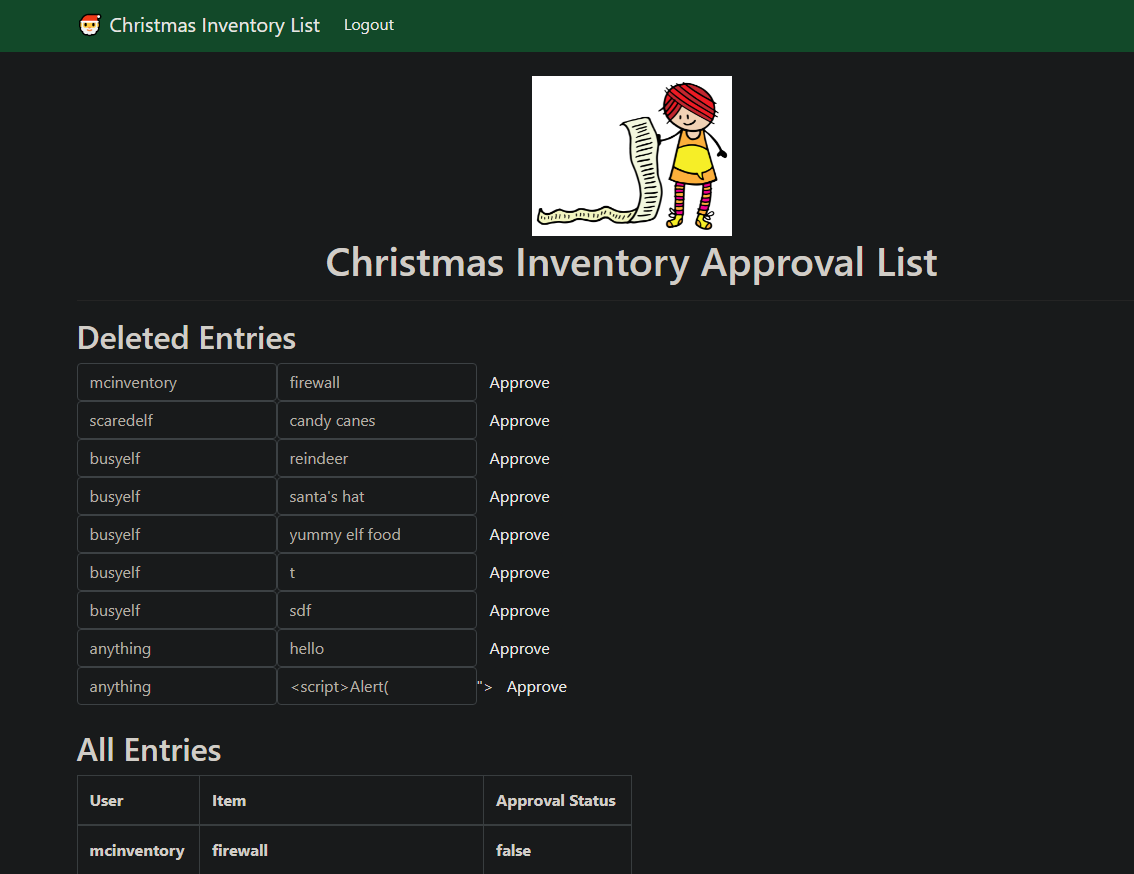
If we are able to put that cookie in our request we can easily able to login into the mc inventory user and we can do this with burp suit but I do not do that I'm registering another account with a random email and password but use a username mcinventory there and when I login into that account and we can log in into mcinventory user and there we can see the mcinventory request
Task 7 [Day 2] Arctic Forum

A big part of working at the best festival company is social live! The elves have always loved interacting with everyone. Unfortunately, the Christmas monster took down their main form of communication - the arctic forum!
Elf McForum has been sobbing away McElferson's office. How could the monster take down the forum? In an attempt to make McElferson happy, she sends you to McForum's office to help.
P.S. Challenge may take up to 5 minutes to boot up and configure!
Access the page at http://[your-ip-here]:3000
Check out the supporting material here!
Answer the questions below
Q1: What is the path of the hidden page? A: /sysadmin Solution To get the hidden page of the web we can use any directory scanning tool in my case I use ffuf because of its fast speed and I use wordlist directory-list-2.3-small.txt with the following command
This will show so many hidden directory/pages but there are two pages that have status code 200 and one of them are the answer you can filter the ffuf result by only show status code 200 with the switch -fc 200 so this will show you only the result that has status 200 so one of them is your answer
Q2: What is the password you found? A: defaultpass Solution Now we have access to the hidden page and they are admin panel where we can login to the admin account But we have to find a valid admin credential to solve that so when I see the source code of that page there is some interesting comment
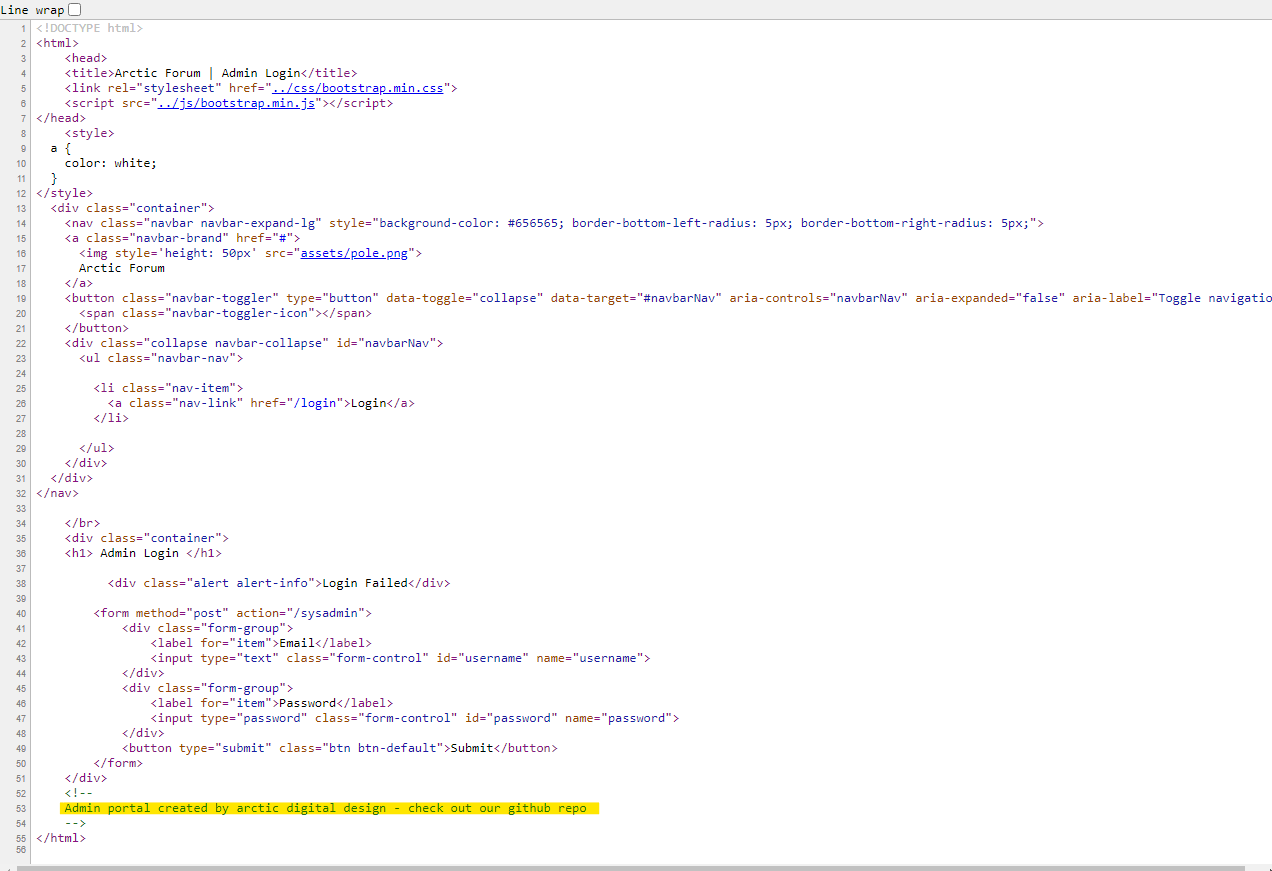
That gives us a clue of who made this admin panel so when we search that Repo in Google found the following
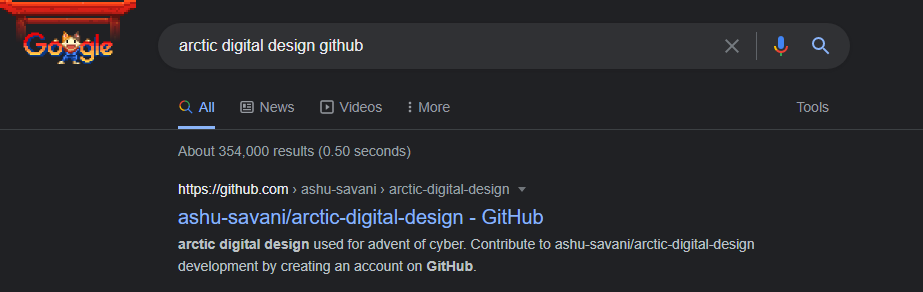
In that repo, we found a valid credential. Q3: What do you have to take to the 'partay' A: Eggnog Solution After login into the admin page, there is a text box where we found the solution to the above question
Task 8 [Day 3] Evil Elf

An Elf-ministrator, has a network capture file from a computer and needs help to figure out what went on! Are you able to help?
Supporting material for the challenge can be found here!
Answer the questions below
Q1: What's the destination IP on packet number 998? A: 63.32.89.195 Solution Download the Evil Elf.pcap file and open it in Wireshark now there are a lot of packets scroll down all the way to packet no 998 and there you found the destination IP Address

Q2: What item is on the Christmas list? A: ps4 Solution Now in the filter bar type Telnet and press enter this will filter out all the packets and show you only a telnet packet there only three packets are there so right-click on the first packet and it will open a drop-down menu and then hover into Follow and then select Follow TCP stream and you will see two commands there first one has the answer
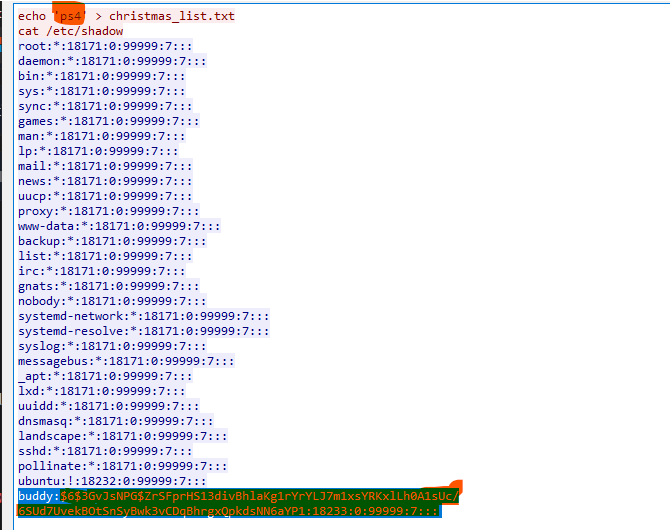
Q3: Crack buddy's password! A: rainbow Solution In the previous step, we see the attacker use the cat command to see the content of the shadow file there we can see the buddy user so now we can crack its hash with john or hashcat but in my case I use john. So first copy that hash and save it to a file for example that name is hash.txt so we can use the rockyou.txt wordlist file to crack that hash with the following command
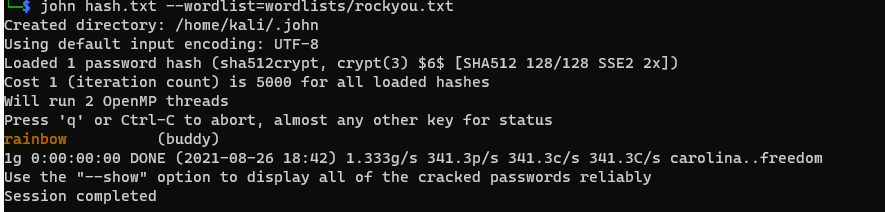
After the cracking is finished we can see the cracked password there
Task 9 [Day 4] Training

With the entire incident, McElferson has been very stressed.
We need all hands on deck now
To help resolve things faster, she has asked you to help the new intern(mcsysadmin) get familiar with Linux. Access the machine via SSH on port 22 using the command
ssh mcsysadmin@[your-machines-ip]
username: mcsysadmin password: bestelf1234
Check out the supporting material here
Answer the questions below
Q1: How many visible files are there in the home directory(excluding ./ and ../)? A: 8 Solution Use the ls command when you login with ssh this will show you all the files in the home directory
Q2: What is the content of file5? A: recipes Solution Use the cat file5 command to see the content of file5.
Q3: Which file contains the string ‘password’? A: file6 Solution Use the following command to get the file that has a string password in it
Q4: What is the IP address in a file in the home folder? A: 10.0.0.05 Solution Use cat * | grep 10. this command and they will show you all the content that has 10. there you can see an IP address
Q5: How many users can log into the machine? A: 3 Solution Use the cat /etc/passwd or cat /etc/passwd | grep /bin/bash command to see the content of passwd that contains information about all the users in the system. There you will see three users have shell /bin/bash that user can log in to the system
Q6: What is the sha1 hash of file8? A: fa67ee594358d83becdd2cb6c466b25320fd2835 Solution Use sha1sum file8 to get the sha1 hash of file8
Q7: What is mcsysadmin’s password hash? A: $6$jbosYsU/$qOYToX/hnKGjT0EscuUIiIqF8GHgokHdy/Rg/DaB.RgkrbeBXPdzpHdMLI6cQJLdFlS4gkBMzilDBYcQvu2ro/ Solution Use the following command
This command search for shadow file backup in the system and give you the location where that backup file exists.When you found that use the following command to get the content of that file
There you will see that hash of mcsysadmin user password hash.
Task 10 [Day 5] Ho-Ho-Hosint

Elf Lola is an elf-of-interest. Has she been helping the Christmas Monster? let's use all available data to find more information about her! We must protect The Best Festival Company!
Resources available here.
Answer the questions below
Q1: What is Lola's date of birth? Format: Month Date, Year(e.g November 12, 2019) Hint: What information can you get from ExifTool? Are they using the same Creator name on any social networks... Twitter Perhaps? A: December 29, 1900 Solution First, download the image from tryhackme and also download exiftool with the following command
When you have both then use the following command to get the metadata of the image that you download from tryhackme
their output is like this
As you can see from the creator section they have something like a username in it. So we can go to osintframework that have many utilities to do open source intelligence from there we can select the username section and then select instant username search or some other username search so we know which platform has this username available or which have not. Those who do have not available that username that means someone has that username on that site so we can search for that username on that platform to get some information about that user. There is also a tool for this name sherlock you can install it using sudo apt install sherlock that also searches for usernames. There we got that this username(JLolax1) is registered on Twitter so we can go there and there we got the birth date of Lola
Q2: What is Lola's current occupation? A: Santa's Helpers Solution From Lola's Twitter account, we also got its current occupation.
Q3: What phone does Lola make? A: iPhone X Solution From Lola's Twitter account Tweet we got the phone that Lola makes.
Q4: What date did Lola first start her photography? Format: dd/mm/yyyy Hint: How many years ago did she start? Have you tried using the WayBackMachine? A: 23/10/2014 Solution From Lola's Twitter account, we got Lola's Personal website when we go there we don't get anything related to when Lola start Photography so to know about this we go to the website called waybackmachine WaybackMachine This is a website that takes snapshots of the website so we can see how it looked in past. That is like a web archive. so when we search the Lola website on there we know about the waybackmachine took 65 snapshots between October 23,2019 and July 9,2021
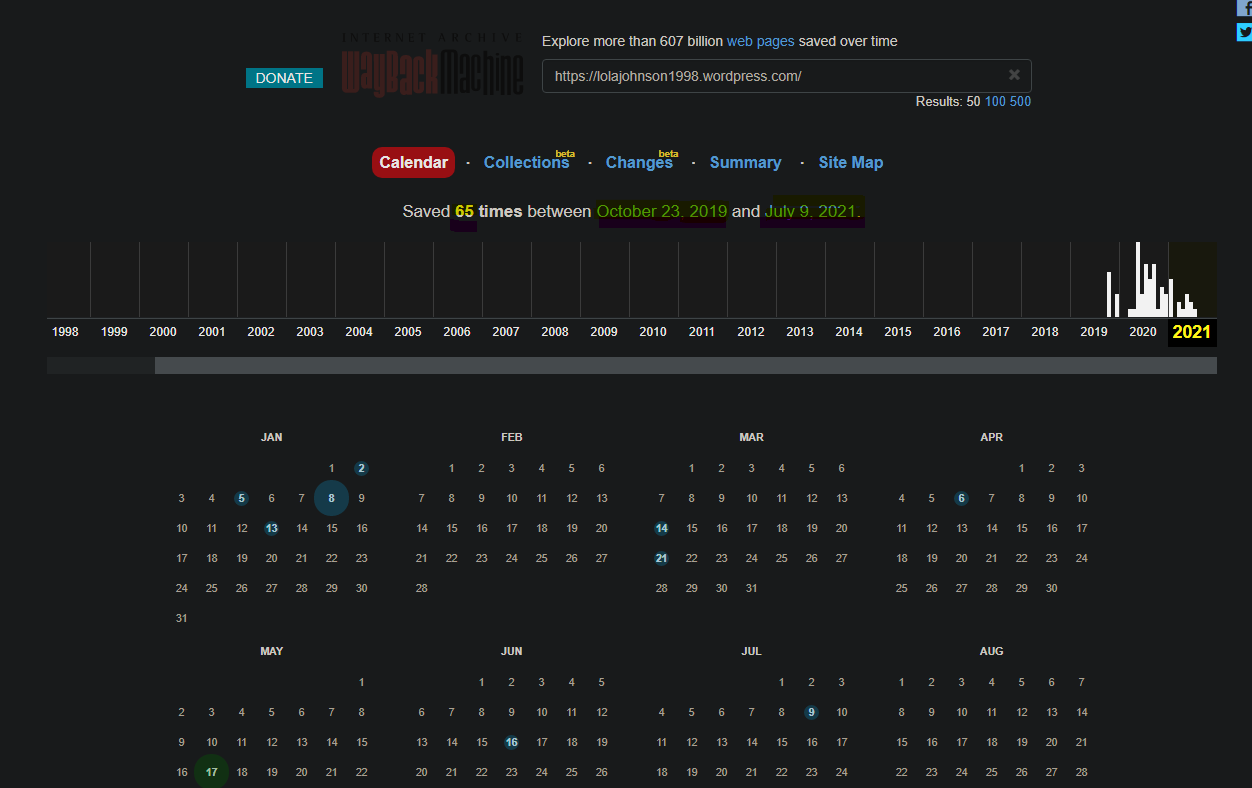
So when we check the snapshots of its website from October 23,2019 we see the following output there
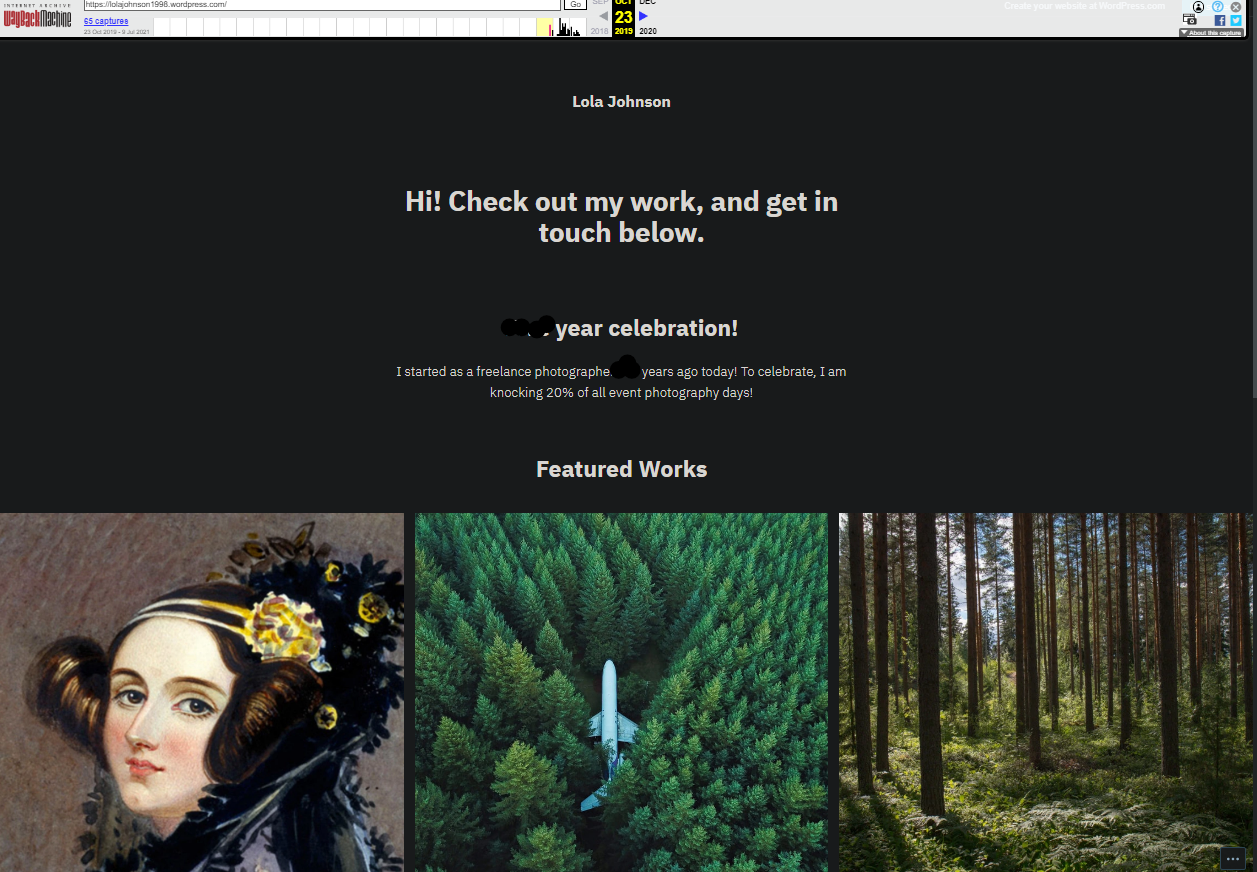
There we get Lola to start Photography some year back from October 23,2019 so when we minus that year from 2019 we go to the answer
Q5: What famous woman does Lola have on her web page? A: Ada Lovelace Solution On Lola's website, all snapshots have one photo in common and that is

So we can go to Google image search for doing a reverse image search to get that information about this image there we can paste the URL of the image or we can upload the image to get the information
Task 11 [Day 6] Data Elf-iltration

"McElferson! McElferson! Come quickly!" yelled Elf-ministrator.
"What is it Elf-ministrator?" McElferson replies.
"Data has been stolen off of our servers!" Elf-ministrator says!
"What was stolen?" She replied.
"I... I'm not sure... They hid it very well, all I know is something is missing" they replied.
"I know just who to call" said McElferson...
Check out the supporting material here.
Challenge and supporting material created by Sq00ky.
Answer the questions below
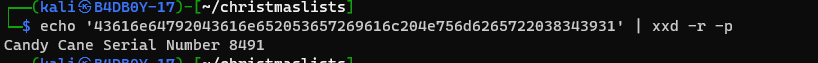
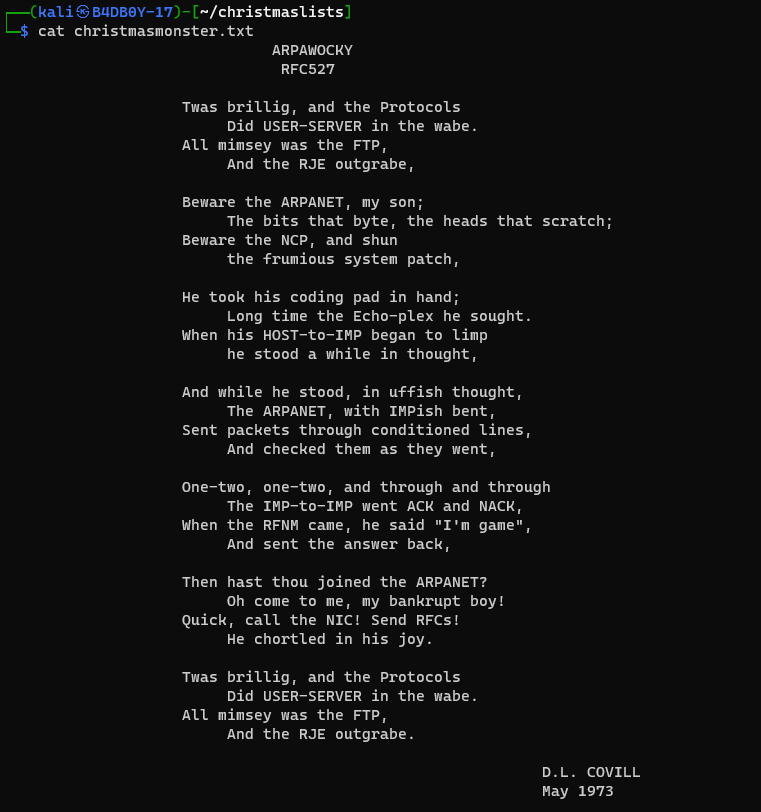
Q1: What data was exfiltrated via DNS? A: Candy Cane Serial Number 8491 Solution TryHackme give us a pcap file that has intercepted traffic when we open it on the Wireshark we can see there is so many DNS request generated that have some hex encoded value and that is going to holidaytheif.com
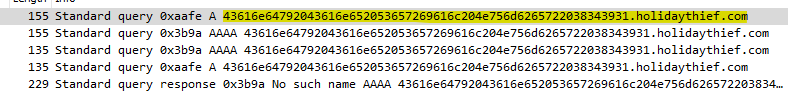
So when we decode that hex value using the command
we can see the exfiltrated data attacker send
Q2: What did Little Timmy want to be for Christmas? A: pentester Solution Scroll down a little more in Wireshark we also see there is some http request also that have some file so we go to wireshark export section to get that file so we can save that file for further forensic
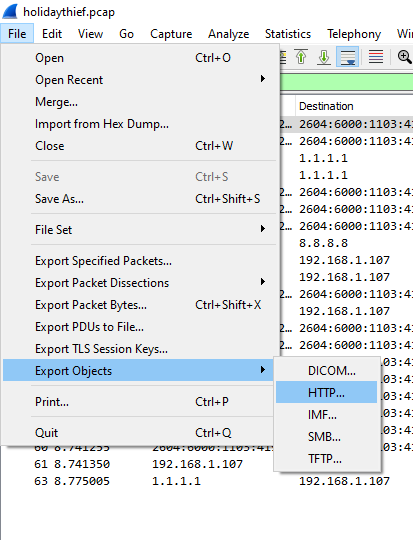
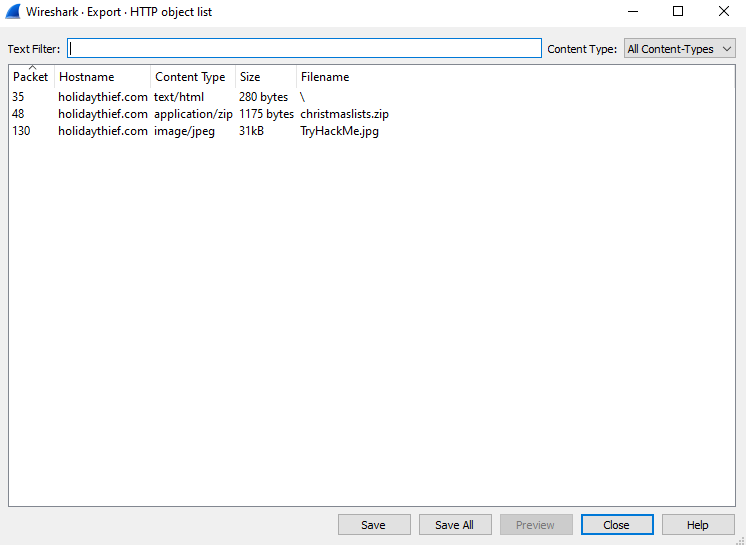
After saving that file we can see there are two files there one is an image and the other is a zip file. When we open the image file that is simply a tryhackme logo image so we use steghide to check if they have some hidden data on it so use the following steghide command
and give the password empty and we got the following output
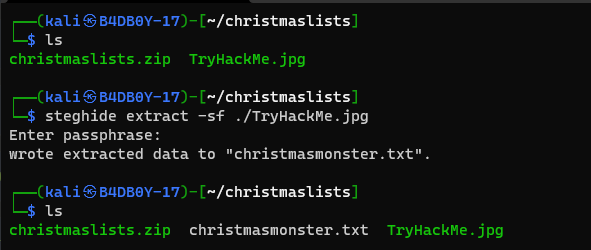
that save the hidden data on a file name christmasmonster.txt. Now we move to the zip file and there is many text file there but they have a password protected so we use the fcrackzip tool to crack that zip file password with the following command
this gives us the following output.
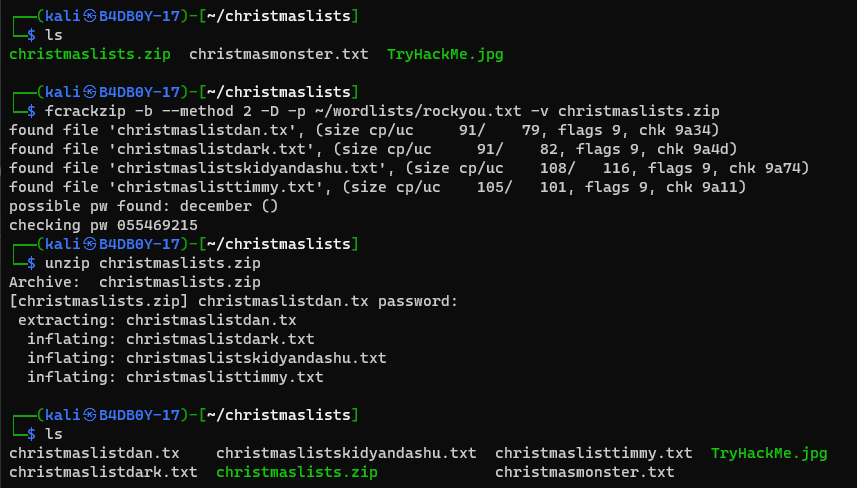
After trying that password we successfully unzip the files and there is a file that has name christmaslisttimmy.txt when we cat that file we got the following output
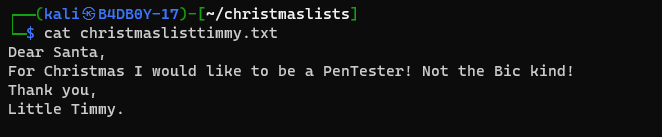
They have our answer
Q3: What was hidden within the file? A: RFC527 Solution In the Previous Question we use steghide to get the hidden data on the image file we got and they save that data on a file name christmasmoster.txt when we cat that file there we got our answer on the second line.
Task 12 [Day 7] Skilling Up

Previously, we saw mcsysadmin learning the basics of Linux. With the ongoing crisis, McElferson has been very impressed and is looking to push mcsysadmin to the security team. One of the first things they have to do is look at some strange machines that they found on their network.
Check out the supporting material here.
Answer the questions below
Q1: how many TCP ports under 1000 are open? Hint: Use -p port_start - port_end to specify a range A: 3 Solution Nmap Scan Reports
Q2: What is the name of the OS of the host? A: Linux Solution Nmap will not guess the exact OS but they will show you some guesses of OS there you will find the answer
Q3: What version of SSH is running? A: 7.4 Solution We can see from the above Nmap Scan Result ssh version is OpenSSH 7.4 (protocol 2.0)
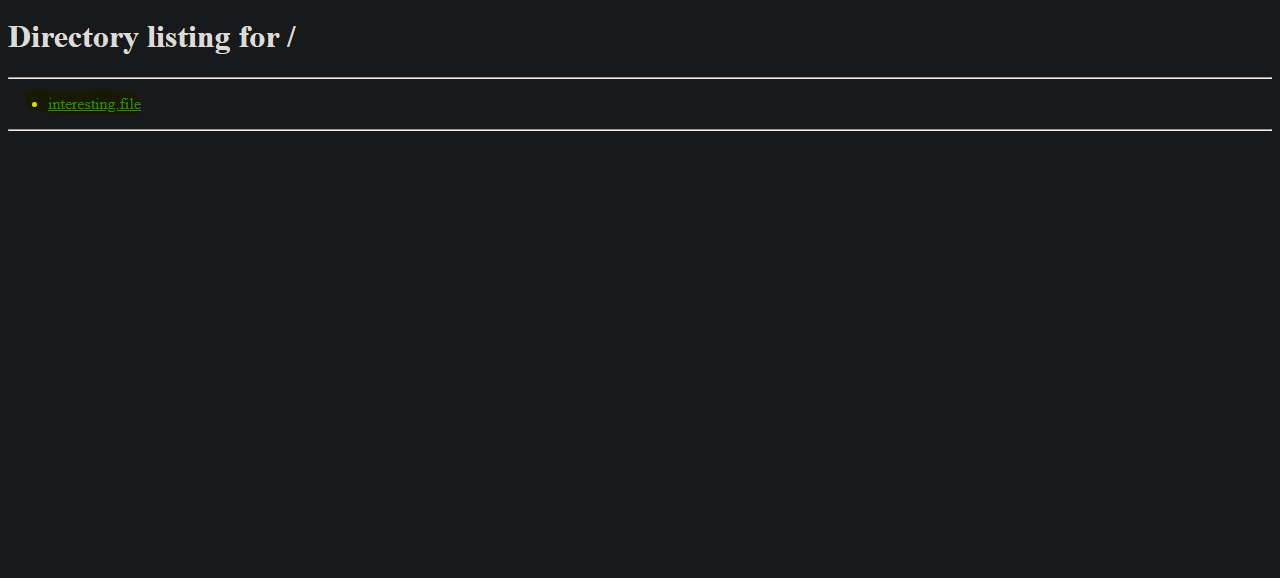
Q4: What is the name of the file that is accessible on the server you found running? A: interesting.file Solution As we can see from the scan report there is an http service running on port 999 so when we go to that location in the browser using http://<IP_Address_here>:999 we can see the file that is accessible there.
Task 13 [Day 8] SUID Shenanigans

Elf Holly is suspicious of Elf-ministrator and wants to get onto the root account of a server he set up to see what files are on his account. The problem is, Holly is a low-privileged user.. can you escalate her privileges and hack her way into the root account?
Deploy and SSH into the machine.
Username: holly
Password: tuD@4vt0G*TU
SSH is not running on the standard port. You might need to nmap scan the machine to find which port SSH is running on.
nmap <machine_ip>_ -p _<start_port>_-_<end_port>
Read the supporting materials here.
Answer the questions below
Q1: What port is SSH running on? Hint: 65534 is the port number. But can you find out how to log in via SSH on this port? A: 65534 Solution First Run all port scans in any port scanner but I use nmap with the following command
After that, the output is like this
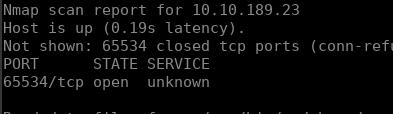
They show the port that has service running now we can connect to it using the following command
Q2: Find and run a file as igor. Read the file /home/igor/flag1.txt A: THM{d3f0708bdd9accda7f937d013eaf2cd8} Solution Now when we login to ssh we use the ls command on the /home/igor user directory and we see there is a file name flag1.txt but we cannot see its content using the cat command because we do have not enough permissions to read it so we find some SUID binaries using the following command
and we get the following output
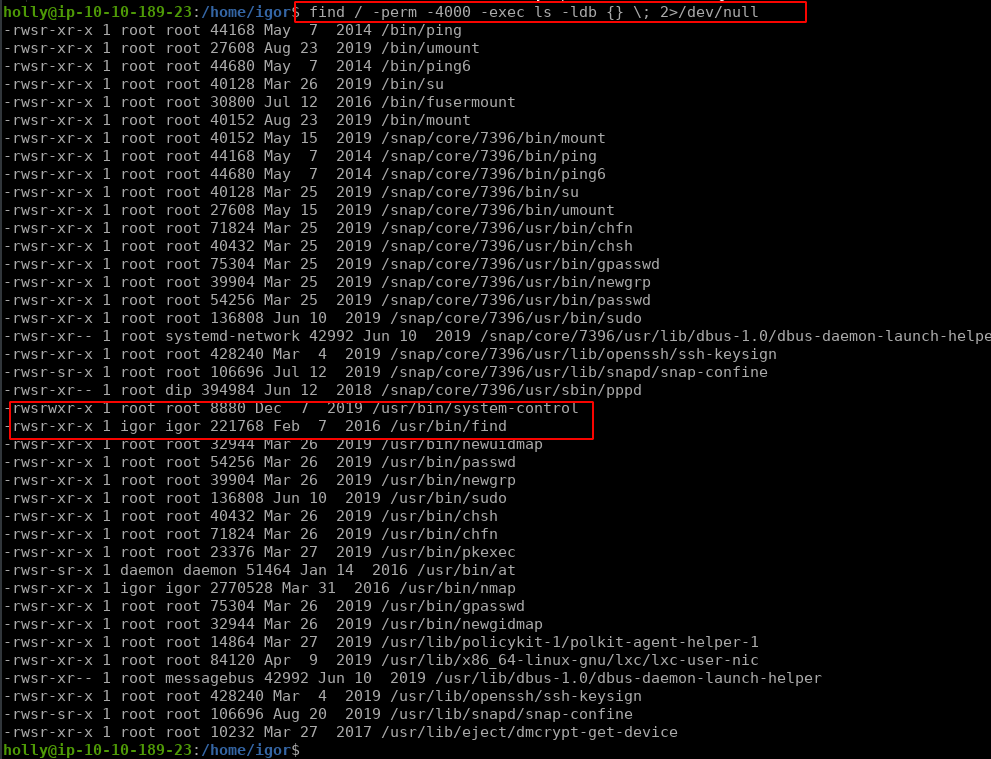
There we see the find command has a SUID bit set and they are owned by the igor user so we can use it to read flag1.txt from its home directory using the following command
This will show us that flag
Q3: Find another binary file that has the SUID bit set. Using this file, can you become the root user and read the /root/flag2.txt file? Hint: It may simply look like a standard Linux binary file. And no, it's not the Nmap binary on the machine. A: THM{8c8211826239d849fa8d6df03749c3a2} Solution
From the output of SUID, we find above we see there is a binary name /bin/system-control. When I run it they prompt me to run a command and when I use the id command there. I see they run the command as root so I run again that binary and use the bash command so I got the bash shell with root privileges so now I use the cat /root/flag2.txt command to see the root flag.
Task 14 [Day 9] Requests

McSkidy has been going to keep an inventory of all the infrastructure but he finds a random web server running on port 3000. All he receives when accessing '/' is
{"value":"s","next":"f"}
McSkidy needs to access the next page at /f(which is the value received from the data above) and keep track of the value at each step(in this case 's'). McSkidy needs to do this until the 'value' and 'next' data have the value equal to 'end'.
You can access the machines at the following IP:
10.10.169.100
Things to note about this challenge:
The JSON object retrieved will need to be converted from Unicode to ASCII(as shown in the supporting material)
All the values retrieved until the 'end' will be the flag(the end is not included in the flag)
Check out the supporting material here.
Answer the questions below
Q: What is the value of the flag? A:
Task 15 [Day 10] Metasploit-a-ho-ho-ho

Once deployed, the machine will take 4 to 5 minutes to boot and configure. Please be patient.
Hi, Lindsey here. I've been a great Elf all year, but there was one incident and now I think I'm on Santa's naughty list.
What? You didn't think we elves got presents too? Well, we do and we get the first pick of the pressies!
Can you help me hack into Santa's system that keeps track of the naughty and nice people to see if I am on it?
 ](https://blog.tryhackme.com/metasploit/)
](https://blog.tryhackme.com/metasploit/)
Check out the blog post shown above to help you on this task.
Answer the questions below
Q1: Compromise the web server using Metasploit. What is flag1? A: THM{3ad96bb13ec963a5ca4cb99302b37e12} Solution Use msfconsole with exploit/multi/http/struts2_content_type_ognl. Set all the requirements like 'RHOST, RPORT, TARGETURI, LHOST, and LPORT' and set the payload to linux/x86/meterpreter/reverse_tcp and run the exploit they give you meterpreter shell.
When you got that use the shell command to spawn a shell in meterpreter and there use the command find / flag1.txt 2>/dev/null this will show you the directory where they store that flag. use the cat command to read it
Q2: Now you've compromised the web server, get onto the main system. What is Santa's SSH password? A: rudolphrednosedreindeer Solution Now you have access to the shell with meterpreter so now go to the /home/santa directory where they store their ssh credentials in a file use the cat command to read it
Q3: Who is on line 148 of the naughty list? A: Melisa Vanhoose Solution Now you have Santa SSH credentials so close the meterpreter and login into the Santa account using SSH with the following command
When you login successfully use the ls command there and you will see a file name naughty list Use the vi command to open that list in the vim editor so you will see the line numbers or you can use the sed command for just search for specific line number use the following command
Q4: Who is on line 52 of the nice list? A: Lindsey Gaffney Solution Use the same procedure we do in the last question but use file nice_list.txt instead of naughty_list.txt they are on the same directory
Task 16 [Day 11] Elf Applications
McSkidy has been happy with the progress they've been making, but there's still so much to do. One of their main servers has some integral services running, but they can't access these services. Did the Christmas Monster lock them out?
Deploy the machine and start scanning the IP. The machine may take a few minutes to boot up.
Check out the supporting material here.
Answer the questions below
Q1: What is the password inside the creds.txt file? Hint: NFS A: securepassword123 Solution Use the following command to check if there are any NFS share exits
So that command shows me a share so I mount that share to my system using the following command
When I successfully mount that share to my system so I go to the place where I mount that share i.e /tmp/nfs so there I see a file name creds.txt that has a password
Q2: What is the name of the file running on port 21? A: file.txt Solution I login to the ftp service using the following command
Note for the anonymous user you don't need to give any password just leave him empty and press enter there When I log in to ftp there I use the ls command and found the file.txt file I use the get file.txt command to download that file and when I see its content using the cat command found MySQL database credentials.
Q3: What is the password after enumerating the database? Hint: SQL A: bestpassword Solution So now we have credentials MySQL so we connect to it using the following command
when we log in to the database I use SQL queries to enumerate the database
To show all databases
To use the DATA database
To show existing tables in the database
to get everything in the user's tables
By using the above queries I got the admin password
Task 17 [Day 12] Elfcryption

You think the Christmas Monster is intercepting and reading your messages! Elf Alice has sent you an encrypted message. It's your job to go and decrypt it!
Read the supporting materials here.
Answer the questions below
Q1: What is the md5 hashsum of the encrypted note1 file? A: 24cf615e2a4f42718f2ff36b35614f8f Solution Use the following command
Q2: Where was elf Bob told to meet Alice? Hint: gpg key is 25daysofchristmas A: Santa's Grotto Solution Use the following command
Q3: Decrypt note2 and obtain the flag! Hint: private password is hello A: THM{ed9ccb6802c5d0f905ea747a310bba23} Solution Use the following command
Task 18 [Day 13] Accumulate
mcsysadmin has been super excited with their new security role but wants to learn even more. In an attempt to show their l33t skills, they found a new box to play with.
This challenge accumulates all the things you've learned from the previous challenges(that being said, it may be a little more difficult than the previous challenges). Here's the general way to attempt exploitation when just given an IP address:
Start out with an NMAP scan to see what services are running
Enumerate these services and try to exploit them
use these exploited services to get initial access to the host machine
enumerate the host machine to elevate privileges
Credit to DarkStar7471 for creating this challenge! Not all tasks will include supporting material!
Answer the questions below
Q1: A web server is running on the target. What is the hidden directory on which the website lives? Hint: dirbuster 2.3 medium A: /retro Solution Use the following command
Q2: Gain initial access and read the contents of user.txt Hint: Don't leave sensitive information out in the open, even if you think you have control over it. A: THM{HACK_PLAYER_ONE} Solution After going to the website /retro directory and enumerating all the pages.Found a comment page that has a string that looks like some secrets thing like a password
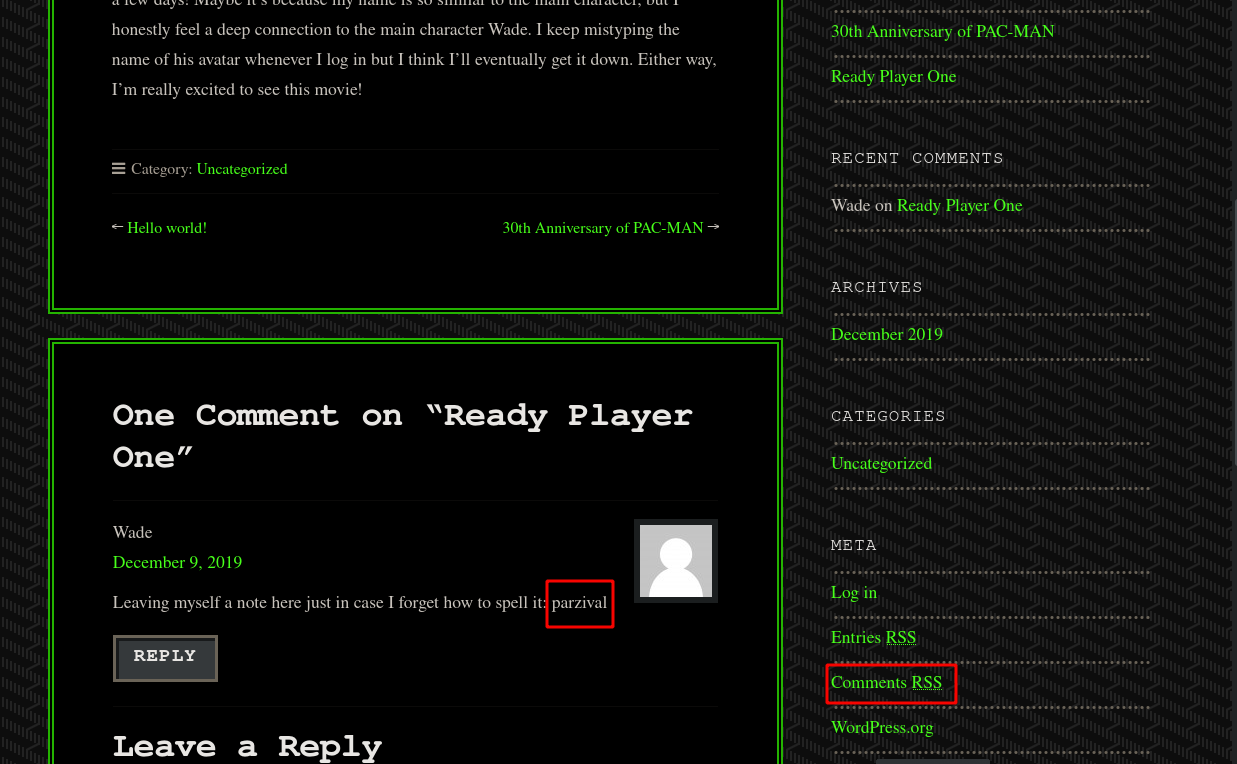
when using that password on the web login page with username:Wade and password:parzival it doesn't work but from the nmap scan report, we found a remote desktop port open so I use that credentials there and they work. We got initial access to the system. Now on the desktop, we can see the user.txt flag
Q3: [Optional] Elevate privileges and read the content of root.txt Hint: Figure out what the user last was trying to find out A: THM{COIN_OPERATED_EXPLOITATION} Solution When I open an internet browser and see the last search site by the user.Found that the user searches for a CVE-2019-1388 that is used for local privilege escalation using the malicious application when Google that vulnerability to know about it more found that video useful. In that system that application is available on its desktop and we follow the above video procedure to get admin privileges. After getting the admin privileges we can see the root flag using the following command
Task 19 [Day 14] Unknown Storage

McElferson opens today's newspaper and see's the headline
Private information leaked from the best festival company
This shocks her! She calls in her lead security consultant to find out more information about this. How do we not know about our own S3 bucket?
McSkidy's only starting point is a single bucket name: advent-bucket-one
Check out the supporting material here.
Answer the questions below
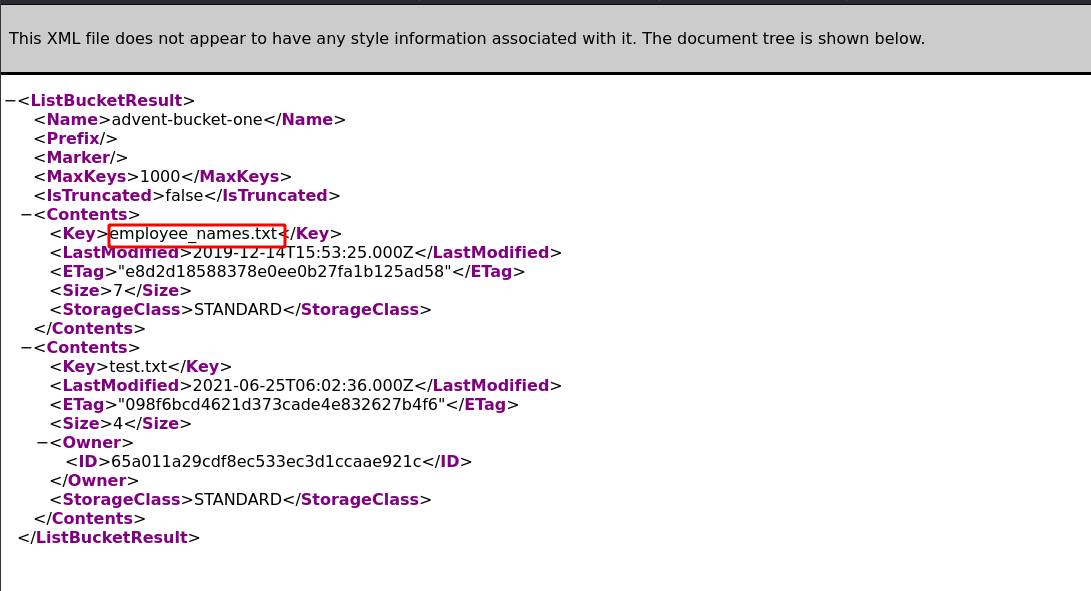
Q1: What is the name of the file you found? A: employee_names.txt Solution THM gave us the Amazon bucket name and that is advent-bucket-one so we can search that bucket using the following URL https://advent-bucket-one.s3.amazonaws.com/ This URL shows us the output like following
Q2: What is in the file? A: mcchef Solution So now we see the key employee_names.txt from the previous question so now we can see its content using the following URL https://advent-bucket-one.s3.amazonaws.com/employee_names.txt
Task 20 [Day 15] LFI

Elf Charlie likes to make notes and store them on his server. Are you able to take advantage of this functionality and crack his password?
Read the supporting materials here.
Answer the questions below
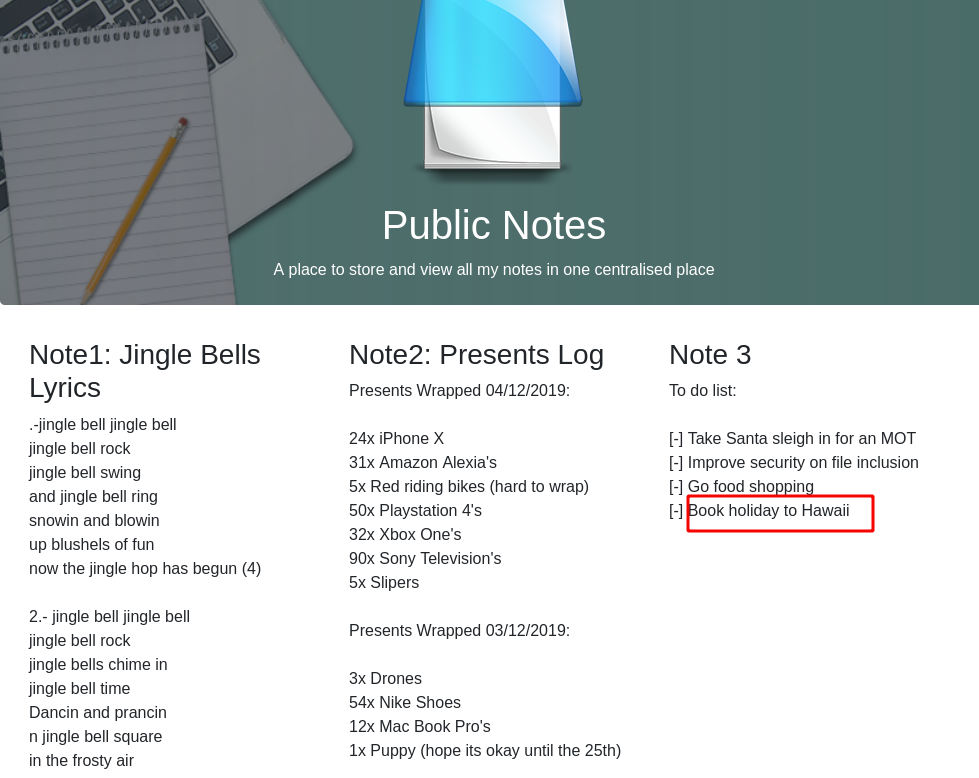
Q1:What is Charlie going to book a holiday too? A: Hawaii Solution Visit the website and its first page have the answer
Q2: Read /etc/shadow and crack Charlies password. A: password1 Solution Go to the following link to get the shadow file http://IP-Here/get-file/%2fetc%2fshadow When you got the shadow file so you can copy the password hash for charlie user and save it in a file and then use the following command to get the password
Q3: What is flag1.txt? A: THM{4ea2adf842713ad3ce0c1f05ef12256d} Solution So from above we have the Charlie password so we can ssh to the system because from the nmap scan report, we see port 22 is open for ssh so we can use it like the following command
Task 21 [Day 16] File Confusion
The Christmas monster got access to some files and made a lot of weird changes_. Can you help fix these changes?
Use a (python) script to do the following:
extract all the files in the archives
extract metadata from the files
extract text from the files
Use the questions to guide you on how to write the script. Check out the supporting material here.
Answer the questions below
Q1: How many files did you extract(excluding all the .zip files) A: 50
Q2: How many files contain Version: 1.1 in their metadata? A: 3
Q3: Which file contains the password? A: dL6w.txt
Solution/Script
I don't know Python so I use bash scripting to solve that problem I also don't know bash scripting that much but they are a little easy because they use Linux command that we use daily so this will solve our problem but I google to know about while-read loop with the help of that I made the following script
Its Output is like this

My fellow A3r1t made a code that is written in Python that solves our problem code like this
And its output is like this

Task 22 [Day 17] Hydra-ha-ha-haa
You suspect Elf Molly is communicating with the Christmas Monster. Compromise her accounts by brute forcing them!
Use Hydra to brute force Elf Molly's password. Use the rockyou.txt password list, which can be found here.
Supporting materials can be found here.
This machine will take between 3-4 minutes to boot.
Answer the questions below
Q1: Use Hydra to bruteforce Molly's web password. What is Flag 1? (The flag is mistyped, it's THM, not TMH). Hint: If you've tried more than 30 passwords from RockYou.txt, you are doing something wrong! A: THM{2673a7dd116de68e85c48ec0b1f2612e} Solution Use the following hydra command to get the login password for the molly user
When you got the credential login to the web and got the flag there
Q2: Use Hydra to bruteforce Molly's SSH password. What is flag 2? A:THM{c8eeb0468febbadea859baeb33b2541b} Solution Use the following hydra command to bruteforce molly user ssh password
When you got the credentials login to ssh using the following command
When successfully login to ssh see the flag in Molly's home directory using the command cat flag2.txt
Task 23 [Day 18] ELF JS
McSkidy knows the crisis isn't over. The best thing to do at this point is to OSINT
We need to learn more about the Christmas monster
During their OSINT, they came across a Hacker Forum. Their research has shown them that this forum belongs to the Christmas Monster. Can they gain access to the admin section of the forum? They haven't made an account yet so make sure to register.
Access the machine at http://[your-ip-address]:3000 - it may take a few minutes to deploy.
Check out the supporting material here.
P.S. If you want to learn more about XSS, we have a room where you can learn about it in depth.
Answer the questions below
Q1: What is the admin's authid cookie value? A: 2564799a4e6689972f6d9e1c7b406f87065cbf65 Solution First, register an account and then login with that account there you have to paste the following payload
After that you have to start a listener netcat is also useful for this but in my case, they don't work fine so I use the following command to start a listener
So now everything is ready now you just have to wait for 2-3 min admin cookie is fetched by your listener.
Task 24 [Day 19] Commands
Another day, another hack from the Christmas Monster. Can you get back control of the system?
Access the web server on [http://[your-ip]:3000/]
McSkidy actually found something interesting on the /api/cmd endpoint.
Check out the supporting material here.
Answer the questions below
Q1: What are the contents of the user.txt file? A: 5W7WkjxBWwhe3RNsWJ3Q Solution Go to the following URL
When we go there we see they run a system command and give us the output of the ls command so we have command execution to the target system we can use it to get a reverse shell or we can just get the flag also but for me, I get reverse shell first with the following URL encoded payload:
This payload gives me a reverse shell with root privileges after that I go to the /home/bestadmin directory and there I got the user flag.
Task 25 [Day 20] Cronjob Privilege Escalation
Do you think the evil Christmas monster is acting on Elf Sam's account?
Hack into her account and escalate your privileges on this Linux machine.
There is no supporting material - the only new concept in this challenge is Linux cronjobs. Join our Discord if you're really struggling.
Answer the questions below
Q1: What port is SSH running on? Hint: Use nmap to enumerate services on ports 4000 and 5000. A: 4567
Q2: Crack Sam's password and read flag1.txt Hint: Complete the challenge on day 17, to understand how to use Hydra. A: THM{dec4389bc09669650f3479334532aeab} Solution So Here we know the username sam but we don't know the password for that user so we use Hydra to brute force that user's password if the password is weak we can easily crack that password. But we have to note ssh service is not running on the default port so we have to specify the port number with the -s flag. And the final command is the following:-
Its output is like this
Here we got the sam user password chocolate.
Now connect to ssh using the following command
Now you connect to the ssh and read the flag using the command cat flag1.txt.
Q3: Escalate your privileges by taking advantage of a cronjob running every minute. What is flag2? A: THM{b27d33705f97ba2e1f444ec2da5f5f61}
Solution So Now we got flag 1 but for getting flag 2 we have to do some privilege escalation stuff and from the question, we see we have to do this using cronjobs so to do that first I use the following command to see cronjobs for the system cat /etc/crontabs but there I did not get anything use full so I run linpeas for getting some privilege escalation vectors and I see there is also another user on the system name ubuntu so I go there and see flag2.txt in their home directory but they are only readable by that user. But in the home directory, I see a directory name scripts and when I go there, I see a bash script owned by a ubuntu user they are read and writeable to everyone so I think that the user set cronjob that script and when I see its content they are removing everything from /tmp directory so I edit that script and enter a reverse shell command there so I got a reverse shell and after one min I got the shell and now I can see the flag2.txt
Task 26 [Day 21] Reverse Elf-ineering
McSkidy has never really touched low-level languages - this is something they must learn in their quest to defeat the Christmas monster.
Download the archive and apply the command to the following binary files: chmod +x file-name
Please note that these files are compiled to be executed on Linux x86-64 systems.
The questions below are regarding the challenge1 binary file.
Read the supporting materials here.
Answer the questions below
Q1: What is the value of local_ch when its corresponding movl instruction is called(first if multiple)?
A: 1
Solution
Download the task file and there we got two files file1 and challenge1 here file1 is the file you can use to follow the supporting material to understand how to do tasks in radar2 aka r2. when you are familiar with r2 then you use your knowledge in the challenge1 file to solve the answer. So now do the task by first opening the chanllenge1 file in r2 with the following command
This will open it in debugged mode and after that, the next command we use is aa Which will analyze the binary.
When they will complete using the command afl this will analyze the function and list it. They show us many functions so we can grep specific functions like main using the following command

Here we see the main function in the output so now we can use the following command to view its summary
and output is like this

There we see three variables var_ch var_8h and var_4h so our question is to find the value of local_ch that represents var_ch Here so do the following steps to find its value first we have to set breakpoints using the following command syntax
So according to the question, we have to set three breakpoints first on the following line
The second one is here
And third one is here
So we can use its memory address in the db command syntax and after setting all the breakpoints we get the following output

We see all the breakpoints address have a small b after them so that means our breakpoints is set now we can run the binary with the command dc they will run the binary and stop on our first break point so now we use the following command syntax
This shows is variable value in hex so the above command is like this

Here we see the hex value is only 0000 so use the ds command now to compile one step after the breakpoint and again use the px @rbp-0xc command and we see the following output now

And we got the first variable value and it is 1
Q2: What is the value of eax when the imull instruction is called?
A: 6 Solution
So Now we use the same procedure again for the second break point use the dc command to compile the second break point we set and again use pdf@main we see we are now at the second break point and now we ds command to compile one step after and now we use dr command because we are now interested to see register value, not a variable so we use dr command and we see our register value is like this

And there we see the register value is 6 in the last that's its value
Q3: What is the value of local_4h before eax is set to 0?
A: 6 Solution Now again use dc to compile the third breakpoint and use pdf@main to see the breakpoint now use the px command with a fourth variable address as we do in the first step to see its value like this
and our output is like this

and we see the variable hex value has 6 and that our answer
Task 27 [Day 22] If Santa, Then Christmas
McSkidy has been faring well so far with assembly - they got some inside knowledge that the Christmas monster is weaponizing if statements. Can they get ahead of the curve?
These programs have been compiled to be executed on Linux x86-64 systems.
Check out the supporting material here.
The questions below relate to the if2 binary.
Answer the questions below
Q1: what is the value of local_8h before the end of the main function?
A: 9
Solution
To find the answer to this task we have to know about if statements syntax and also understand how they work on assembly language also in assembly language they use jumps to control the structure we know about it on supporting materials TryHackMe made for us above. Download the task file and open supporting material and use if1 binary to follow along with supporting material. When you are good at that then use your knowledge to solve this task as follows
first, open the binary in radara2 binary with the following command
after that use the following command in r2
After that use the aaa command to analyze the program when this is done use the afl command to analyze the functions, they show you so many functions that you can use afl | grep main instead. Now you see the main function there so use the pdf@main command to see the main function and try to understand the program.

The image above shows that there are two variables var_8h and var_4h the first var_8h stores a value of 8 in it and var_4h stores a value of 2 in it. After that var_8h value is transferred to the eax register so the eax register now has the value 8 in it. After that, we see two jumps in the program also jle and jmp we can know about that jumps in supporting materials

So jle is the jump that checks if the condition is less or equal and jmp is the unconditional jump. We can see one statement above jle jump there is a statement like following
cmpl is checking/comparing the var_4h with the eax register.Note var_4h have value 2 and eax have value 8. So they compare if 2 is less or equal to 8 and we know they are not less or equal to 8 so this jump will not execute and execution moves forward one step ahead and we see the statement like following
they add 1 in var_8h that has value 8 in it so after that their value is 9 and that is our answer to this question.
Q2: what is the value of local_4h before the end of the main function?
A: 2
Solution
After adding the value 1 in var_8h there is a jump statement that is an unconditional jump in the program so program control now moves to the following statement
And that clears the value of eax with 0 and after that, there is just the ending instruction for the program so the var_4h value does not change at the ending of the program so var_4h has a value of 2 in it.
But this is just a theory we do to check if this is correct we have to set up break points in the program with the db command with the memory location where we want to add breakpoints. We add break points in the program for both jumps.

From the above image, we see how it looks like when we set up a breakpoint in the program so when the program executes execution is now broken in the first line where we set up the breakpoint. We can see it when we execute the program with the dc command in r2 they compile the program. Now the program is compiled and their execution is stopped in the jle jump so we can see the values of var_8h,var_4h, and eax register like this

there we use the px @<var_8h r2 memory location> and px @<var_4h r2 memory loacation> commands to see the value of the variables in memory and that is in the form of hex. And we use the dr command to see registers values and there we see the rax register value which is the eax register its register value is in the form of register values but they are 8 we see in the end. That's all the values of the variable that are in memory before the first break point we set on the first jump in the program. Now we use the ds command to execute one statement after the break and now if we use again px @<var_8h r2 memory location> command we see the var_8h has now a value of 9 instead of 8 because their value is now incremented because of the following statement
Now we use the dc command to execute the program again but now our execution break is set on the second jump and then we use the ds command to execute one statement ahead of the break and check all the variables values again using the above method we use and we see eax register now have value 0, var_8h have value 9 and var_4h have value 2 and after that program ends so now we practically see the values of the variables also.
Task 28 [Day 23] LapLANd (SQL Injection)
Santa’s been inundated with Facebook messages containing Christmas wishlists, so Elf Jr. has taken an online course in developing a North Pole-exclusive social network, LapLANd! Unfortunately, he had to cut a few corners on security to complete the site in time for Christmas and now there are rumors spreading through the workshop about Santa! Can you gain access to LapLANd and find out the truth once and for all?
This machine may take up to 5 minutes to boot and configure.
Supporting material available here.
Answer the questions below
Q1: Which field is SQL injectable? Use the input name used in the HTML code. Hint: SQLMap will highlight which field is vulnerable if you decide to use it.
A: log_email
Solution
Use the Above sqlmap command to enumerate target databases there
-uis used to specify Target URL--dbsis used for enumerate databases in DBMS--dbms="MySQL"is used to specify the target system is using MySQL database--formsis used to specify we are targeting the form in the target URL--batchis used to specify Never ask for user input, use the default behavior
When this command runs they search every method to do SQLi and they take a while when it found the SQLi vulnerability they search all available Databases in DBMS and after that shows you all the databases like the following

There we see the payload sqlmap used to check if is it vulnerable or not and when they found out that then they search all the databases in DBMS and then show us all the result
Q2: What is Santa Claus' email address? Hint: If your injection is going very slowly, consider enumerating only the information you need instead of trying to dump the whole database.
A: bigman@shefesh.com
Solution
Now we got the Databases in DBMS so we have to see which database is used in LapLand and we see there is a social database so we target that to the database. so now we have to know how many tables are in that database so we use the following command to get the total number of tables in the social database
There
-uis used to specify Target URL--dbms="MySQL"is used to specify the target system is using MySQL database--formsis used to specify we are targeting the form in the target URL-Dis used to specify the Database name we want to target here it issocial--tablesis used to specify and enumerate all the tables in the mentioned database--batchis used to specify Never ask for user input, use the default behavior
So when this command run they do SQLi again by finding the injection vector first and then enumerating mentioned database tables and showing us all the result like following

There we see all the tables in the social database and we see there is a users table so now we target that table and enumerate the total number of columns in that table with the following command
There
-uis used to specify Target URL--dbms="MySQL"is used to specify the target system is using MySQL database--formsis used to specify we are targeting the form in the target URL-Dis used to specify the Database name we want to target here it issocial-Tis used to specify the Table name in the mentioned database--columnsis used to specify enumerate total columns in mentioned table--batchis used to specify Never ask for user input, use the default behavior
When this command runs they show us all the columns in mentioned tables and database like following

There we see all the columns in the table so now we can dump all the data in that columns using the following command
There
--dumpis used to specify dump all the data in the mentioned table When this command runs they show us every data in the table like the following

There we all the columns that we enumerate previously but now we also got its content and there we see all user's email, Name, usernames and password hash, etc
Q3: What is Santa Claus' plaintext password? Hint: It's in rockyou.txt - also try online sites such as HashKiller or Crackstation
A: saltnpepper
Solution
Copy Santa Claus password hash and use any password cracking tool like hashcat or john etc to crack it or you can also use the online site crackstation to crack that hash
Q4: Santa has a secret! Which station is he meeting Mrs. Mistletoe in? Hint: Look at the private messages between users, either through the database or by logging in as Santa!
A: Waterloo
Solution
Now you got the Santa Claus's email and password from the previous task so now you can use that to login to Santa's account in Lapland.After login go to the message section to see Santa's private messages to get the answer
Q5: Once you're logged in to LapLANd, there's a way you can gain a shell on the machine! Find a way to do so and read the file in /home/user/ Hint: If you're getting an error about a file format being blacklisted, try looking up alternative file extensions that will still execute.
A: THM{SHELLS_IN_MY_EGGNOG}
Solution
Now you have a Santa account so you can upload a PHP reverse shell in the Post section first download the PHP reverse shell from the pentestmonkey/php-reverse-shell - GitHub and edit your system IP Address and Port number you want to get the reverse shell back and save it and try to upload that as a Santa Post. They are not uploaded because they use some blacklist to block the php extension so you can rename that php reverse shell and change its extension with phtml and try to upload it and they work so now start a listener on your system with the port you set in the reverse shell with the following command
After that reload the page or right-click on your php reverse shell post and click on reload the image after you will get the reverse shell back to your listener if not use a different extension like phps, php7, etc
Now you got the reverse shell so now use the following command to see the flag
Task 29 [Day 24] Elf Stalk
McDatabaseAdmin has been trying out some new storage technology and came across the ELK stack(consisting of Elastic Search, Kibana, and Log Stash).
The Christmas Monster found this insecurely configured instance and locked McDatabaseAdmin out of it. Can McSkidy help to retrieve the lost data?
While this task does not have supporting material, here is a general approach to how to go about this challenge:
scan the machine to look for open ports(specific to services running as well)
as with any database enumeration, check if the database requires authentication. If not, enumerate the database to check the tables and records
for other open ports, identify misconfigurations or public exploits based on version numbers
The machine may take up to 5 minutes to boot.
Answer the questions below
Q1: Find the password in the database Hint: how do you search for strings in an elastic search database
A: 9Qs58Ol3AXkMWLxiEyUyyf
Solution
First of all, use Nmap to scan all open port

There we see 6 open ports and two ports have http service running on them but when I go there I don't understand what is used for so I use port 5601 there they host kibana web service I do a Google search to learn about it but I didn't understand anything there but in the management section, we see a console so there we can search some query with a little researching on google found how to do that and use the following query and run it to find the password

Q2: Read the contents of the /root.txt file Hint: use the 3rd open port and a Kibana public vulnerability
A someELKfun
Solution
To find the root flag we have to find a public vulnerability and to do that we have to find which version kibana they host again google it and found that there is a status directory there we see the plugin version to find the version number after finding out that searched for a public vulnerability and found an LFI vulnerability there takes some time to understand what they doing and after that, I use the following URL to get the flag that is present in /root.txt path
Go to that location, there you see the website will hang and not load something but when you go the port 8000 log files are hosted there you can find the root flag but you have to use your Eagle eye there because there are so many things

There is an RCE flaw also and got the following URL there they show some proof of concept also but could not able to execute that because there we don't have a convas menu I think this is for a different version
Task 30 [Day 25] Challenge-less
To everyone who participated in our Advent of Cyber event, we hope you learned something new! There is no challenge on the last day, instead, we ask you to complete a room on TryHackMe and enjoy some time off on Christmas Day!
We will pick the daily prize winners and the main winners on Sunday, so there is still time to complete the challenges and enter yourself!
Last updated
